In this post, we will see the concept of cybersecurity in PLC (programmable logic controllers) in industrial automation systems.
Cybersecurity

In a large automation environment, due to the use of abundant and complex network systems, it is important to protect these systems from cyber prone attacks.
Any leakage in data or snag in hardware can affect these networks to be more vulnerable to attacks.
Unauthorized attacks can lead to permanent damage to the system or theft of data.
Due to all these reasons, cyber-security has now become the main factor in deciding the selection of a PLC in a large network system.
Plant Network in a PLC System
Typically, a network system in industrial automation consists of three layers as shown in the figure.
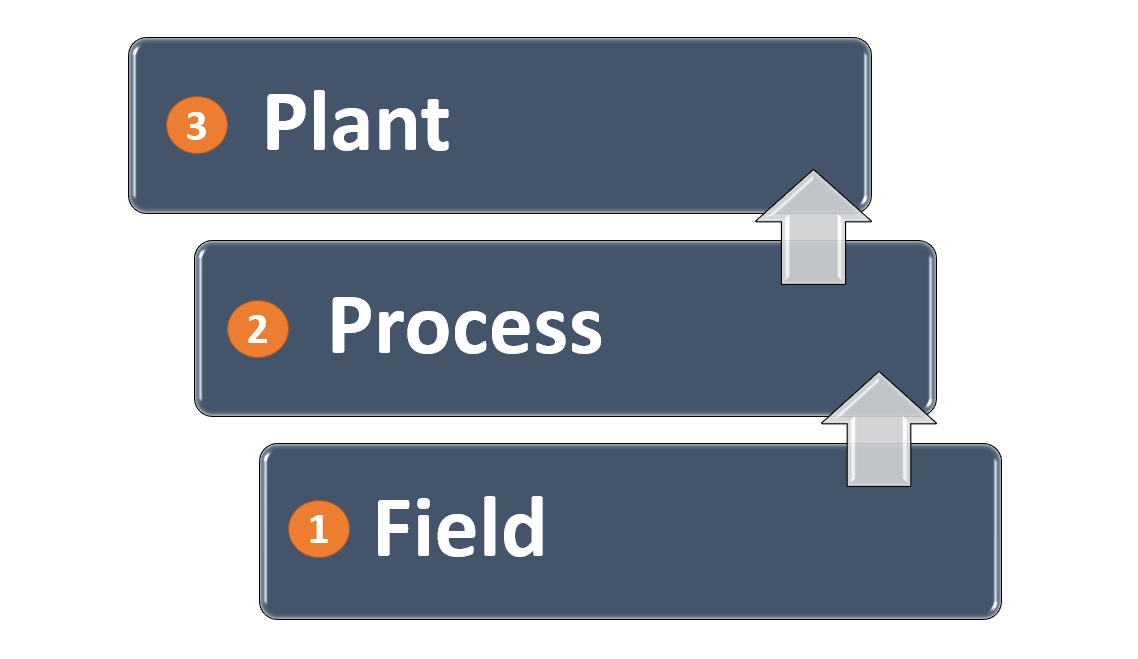
The first layer of the field network is the local IO’s in a field and its local PLC.
The second layer of the process network is the layer of many central PLCs, controlling their corresponding local remote PLCs.
The process layer can have a different range of PLCs. Like, one can be a PLC of Schneider make or the other can be a Siemens make.
The last layer of the plant network is a layer of a centralized SCADA system or Historian PC, controlling the whole plant operation.
Due to large network connectivity at the plant layer, this system is more prone to attacks than a process layer or field layer. This does not mean that these two layers can be given less security.
If the hacker finds out about the leak in this design, he can partially damage the system too by this.
So, overall, each and every device must have protection programs configured in it, to prevent it from hacking. It is just a matter of theory and practice that more layers of protection must be applied to the plant layer.
Types of Security in a PLC system
There are two types of security in a PLC system
- Windows and
- In-Built.
In a Windows PC having software installed in it, one can enforce security in it like disabling an unused network connection, disabling USB ports; which will require only an IT person of the concerned company to unlock it.
Now, the most widely and simple used network connection is a LAN connection. Some of the steps in making a LAN connection secured are disabling all IPv6 stacks, deselecting all LAN properties except QoS Packet Scheduler and IPv4, deselecting LMHOSTS and NetBIOS over TCPIP, etc.
You can also disable remote access connection in windows settings. Microsoft LAN Manager Protocol (LANMAN or MN) and its successor NT LAN Manager (NTLM) have many vulnerabilities in their usage. So, it is also recommended to disabling them.
Generally, in a PLC communication settings tool for LAN connection, there are some standard services like Subnet, FTP, TFTP, HTTP, Port 502, EIP, and SNMP available. All these are used for controlling access to a network.
Accordingly, you need to enable or disable them so that any unauthorized person cannot access the PLC system.
Also, a general rule is to set the network addresses properly and in a certain predefined range. Giving a wider range of addresses by mistake is a big blunder, as this invites other people to access the network.
A basic rule in securing a connection is establishing a strong password. Always enter a password that is not identical and does not relate to anything in the company or the person or the manufacturer. Share it with only the higher-level employees of the plant and ensure that it is not leaked.
Choose a PLC that has CSPN (Certification de Securite de Premier Niveau) certification. It can withstand a cyber-attack driven by 2mmth of skilled hackers. It employs the highest level of secure connections and features that are possible in a PLC, with a wide range of protections.
Like 21CFR compliance used in pharmaceutical industries, PLCs to have their internal event logging or cybersecurity audit for tracking and analyzing connections done. You can exchange these internal events on a network and track them continuously.
These are some of the general features available in a PLC. Different PLCs have different levels of security enhancements.
If you liked this article, then please subscribe to our YouTube Channel for Instrumentation, Electrical, PLC, and SCADA video tutorials.
You can also follow us on Facebook and Twitter to receive daily updates.
Read Next:










Hi Viral, thanks for this. It was a really useful read.
I’m working for an authentication company, and we’re currently developing (actually we’ve developed) an IAM solution for PLC devices.
In fact, we’re currently doing a PoC with one of the largest PLC manufacturers in the world.
Frankly speaking, I would like your expertise in the automation industry and learn more about this industry. If you have time, could I please have a quick chat?
You can email me at tykim@swidch.com
Really looking forward to hearing from you.
Best Regards,
TK