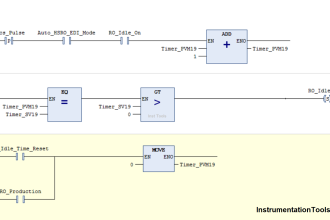
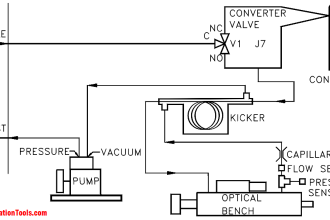
As digital technology finds greater application in industrial measurement and control systems, these systems become subject to digital vulnerabilities.
Cyber-security, which used to be strictly limited to information technology (IT) systems such as those used in office and research environments (e.g. desktop computers, printers, internet routers), is now a pressing concern for industrial measurement and control systems.
There exist many points of commonality between digital IT and digital control systems, and it is at these points where mature protection concepts may be borrowed from the world of IT for use protecting industrial control systems.
However, digital measurement and control systems have many unique features, and it is here we must develop protection strategies crafted specifically for industrial applications.
The chief difference between industrial controls and IT systems is, of course, the fact that industrial controls directly manage real physical processes.
The purpose of an IT system, in constrast, is to manage information. While information can be dangerous in the wrong hands, physical processes such as chemical plants, nuclear power stations, water treatment facilities, hazardous waste treatment facilities, can be even more so.
Cyber-security seems to have its own vocabulary, ranging from unwieldy technical acronyms to slang terms borrowed from amateur computer enthusiasts.
What follows is a partial listing of some common terms and their definitions. This list is not only useful as a definitional reference when encountering such terms in cyber-security literature, but it also serves to outline a number of common attack strategies:
• Active attack: an attack involving data written to a network or to device. See passive attack for contrast.
• Backdoor: an easy-to-access pathway into a system, typically used by system developers for convenience in their work. There is nothing wrong with a backdoor during development, but backdoors are very dangerous when left in place on commissioned systems.
• Blacklist: a database of prohibited messages or users or software applications.
• Broadcast: a form of network where all transmissions are heard by all connected devices, even those devices the data is not intended for. Any communication network sharing a common physical channel is a broadcast network.
• Brute-force attack: attempting every combination of characters in an effort to forge a working password.
• Comsec: shorthand for “communications security”.
• Crypto: shorthand for “cryptography”, which is the purposeful scrambling of data to render it unintelligible to all but the intended recipient.
• Data diode: a device permitting only one-way (simplex) data communication. Data diodes eliminate the possibility of active attacks, because they make writing data to the protected system impossible.
• Denial-of-Service: a form of attack where the intended function of the system is either downgraded or entirely faulted.
• Dictionary attack: attempting common words and character combinations in an effort to forge a working password.
• Firewall: a software or hardware application intended to limit connectivity between networked devices.
• Flooding: an attack technique consisting of overloading a digital system with data or requests for data, generally the point of which being to achieve denial of service (DoS) when the target system becomes overloaded.
• FTP: an acronym standing for File Transfer Protocol, a protocol used for reading and writing files on one computer remotely from another computer. FTP is a predecessor to SFTP which includes public-private key encryption for much better security.
• HTTP: an acronym standing for Hyper Text Transfer Protocol, the method used for computers to exchange web page data (encoded in HTML files). HTTP is not encrypted.
• HTTPS: an acronym standing for Hyper Text Transfer Protocol Secure, the method used for computers to exchange web page data (encoded in HTML files) using encryption.
• IP: an acronym standing for Internet Protocol, the packaging of data into “packets” which may be routed independently of each other across a large network.
• IT: an acronym standing for Information Technology, used to broadly describe general-purpose digital data systems and communications.
• Key: a relatively small segment of digital data that serves to either encrypt or decrypt other digital data. The imagery here is that of a key used to engage or disengage a physical lock.
• LAN: an acronym standing for Local Area Network, a network connecting multiple devices over a limited distance, such as the span of an office building or campus. SeeWAN for contrast.
• Malware: software written with malicious intent.
• Man-in-the-Middle: an attack where the attacker is positioned directly in between sender and receiver, in such a way as to be able to modify messages sent over the network without either sender or receiver being aware.
• Operating system: software installed on a computer for the purpose of directly managing that computer’s hardware resources, functioning as an intermediate layer between the application and the hardware itself.
The existence of operating system software vastly simplifies the design and development of application software. Popular consumer-grade operating systems include Microsoft Windows, Apple OS X, Linux, and BSD.
• Packet sniffing: the act of passively monitoring data transmitted over a broadcast network.
• Passive attack: an attack only involving the reading of data from a network or device. See active attack for contrast.
• Passphrase: an easily-memorized sentence which may be used to generate complex passwords. For example, one could take the first letter of every word in the passphrase “What we have here is a failure to communicate” to generate the password “wwhhiaftc”.
Passphrases are useful because they make complex passwords easy to remember, and in fact may be used to generate multiple passwords from the same phrase (e.g. using the last letter of each word instead of the first, to create the password “teeesaeoe” from the same passphrase used previously).
• Ping: a simple network utility used on IP networks to test connectivity. The ping message is sent from one computer to another, with the receiving computer replying to declare successful receipt of the ping message.
• Private key: a cryptographic key useful for decrypting encrypted data. “Private” refers to the fact that this key must be held in confidence by authorized parties only, since it has the ability to unlock coded messages.
• Public key: a cryptographic key useful only for encrypting data. “Public” refers to the fact that this key may be shared openly, as it cannot be used to unlock a coded message, but instead is only useful for encoding messages sent to a party holding a private key which can decode the message.
• Replay attack: a form of attack where a message is intercepted, recorded, and later broadcast to the network in order to inflict damage. An interesting feature of replay attacks is that they may work on encrypted messages, and even when the purpose of the message is unknown to the attacker!
• SFTP: an acronym standing for Secure File Transfer Protocol, a protocol used for reading and writing files on one computer remotely from another computer. SFTP is a successor to FTP which lacked encryption.
• Sniffing: inspecting network communications for important data. So-called “packet sniffers” monitor data traffic on a broadcast network for certain information such as network addresses and data content.
• Spoofing: presenting a false identification to the receiver of digital data. This commonly takes the form of presenting fake network address information, to trick the receiver into thinking the source is from a legitimate location or device.
• SSH: an acronym standing for Secure Shell, a remote-access utility commonly used in Unix operating systems allowing users to log into a computer from another computer connected to the same network. SSH is a successor to telnet, which lacked encryption.
• TCP: an acronym standing for Terminal Control Protocol, the protocol used to ensure segments of data make it to their intended destinations after being routed by IP (see Internet Protocol ).
• Telnet: a remote-access utility commonly used in Unix operating systems allowing users to log into a computer from another computer connected to the same network. Telnet is a predecessor to SSH which includes public-private key encryption for much greater security.
• Trusted: a component or section of a digital system that is assumed to be safe from intrusion.
• VPN: an acronym standing for Virtual Private Network, which encrypts every aspect of a transaction between two computers connected on a network. The effect is to form a “virtual network” between the machines, the privacy of which being ensured by the encryption used to scramble the data.
• Vuln: shorthand for “vulnerability” or weakness in a system.
• Walled garden: a term used to describe an area of a digital system assumed to be safe from intrusion. See trusted.
• WAN: an acronym standing for Wide Area Network, a network connecting multiple devices over a long range, such as the span of a city.
• War dialing: the exploratory practice of dialing random phone numbers in search of telephone modem connections, which may connect to computer systems.
• Whitelist: a database of permitted messages or users or software applications.