Read Important Networking Interview Questions, Basic Networking questions and answers, TCP/IP questions and answers, Network communications questions.
Important Networking Interview Questions

Explain range of TCP/IP classes
CLASS A = 1 to 126
CLASS B = 128 to 191
CLASS C = 192 to 223
CLASS D = 224 to 239 (Multicasting)
CLASS E = 240 to 255 (Research)
What are Pvt. IP address ?
Pvt. IP are IPs which are not used in Internet or which are not routable in
Internet. They are also called as non-routable IP’s. Class A = 10.0.0.0 to 10.255.255.255
Class B = 172.16.0.0 to 172.31.255.255
Class C = 192.168.0.0. to 192.168.255.255
What is function of Router ?
Router is a device or PC which is used to connect two or more IP networks.
What is Default Gateway :
Default gateway is the address of router.
What is Subnet Mask ?
Subnet mask is used to differentiate Network ID and Host ID from a given IP address. The default subnet mask are as under
Class A = 255.0.0.0
Class B = 255.255.0.0
Class C = 255.255.255.0
What is Loopback address ?
The loopback address is 127.0.0.1. This address is used to check local TCP/IP suite or local machine.
What protocol is used by PING ?
Ping uses ICMP(Internet Control Management Protocol)
What is used of Tracert ?
Tracert is a to find path information between source and destination. It show no. of hops between source and desitination. Tracert also uses ICMP protocol.
Difference between NetBEUI and TCP/IP
TCP/IP vs NetBEUI are
- industry standard Microsoft propertiery
- IP address NO addressing
- supports routing Non routable
- Large network small network
- more confiugration no configuration
What is full form of PING ?
Packet Internet Network Gopher
BASICS OF NETWORKING
Difference between Switch and Hub
Switch
-
- Works at layer 2
- Uses MAC address for packet forwarding
- Does not required CSMA/CD
- Faster than HUB
- Full-duplex
- high throughput
HUB
- works at layer 1
- uses broadcast for packet forwarding
- requires CSMA/CD
- Slower than Switch
- low throughput
- Half-duplex
Explain AT&T color code for straight cable and cross cable
- Orange/white
- orange
- green/white
what is bandwidth of of CAT5 cable
100 Mbps
What is the recommanded CAT5 cable length between switch and PC ?
100 meters
When to use cross cable and straight cable
Similar device = cross cable
switch to switch
PC to PC, Hub to HUB, Switch to HUB,PC to router, router to router
Unsimilar device = straight cable
PC to switch, PC to HUB,Router to Switch
Which pins are used in CAT5 cables
- pin no. 1,2,3,6
- pin 1 = tx +
- pin 2 = tx –
- pin 3 = rx +
- pin 6 = rx –
Difference between domain and workgroup
Domain
- centralized network model
- Domain is controlled by DC
- Centralised login
- centrailsed user database
- Easy and centrailsed management
- good for large network
Workgroup
- decentralized network
- No centrailzed control
- local user databased
- good for small network
- Local login
Different types of LAN topologies
Bus topology = 10base2 (Thinnet) = 10base5 (Thicknet)
Star topology = 10baseT (ethernet, 10 mbps)
= 100baseTx (fastethernet, 100 mbps)
= 100baseFX (fastethernet with Fibre)
= 1000baseTX (gigabit ethernet, 1000 mbps)
= 1000basefx (gigabit ethernet with fibre)
WAN toplogies = PSTN (Public switched telephone network)
= ISDN (Integrated switched digital network)
= Frame Relay
= Leased Line
= DSL (Digital subscriber line)
= ATM (Async Transfer Mode)
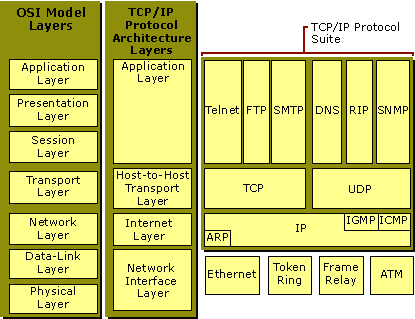
Explain in short about all 7 layers of OSI
Application layer = user interface and application
Presentation layer = Data conversion and transformation
session layer = keep data of diff. application seperately
transport layer = end to end connectivity using port numbers.
network layer = logical addressing like IP address.
Data link layer = Physical addressing like MAC address.
Physical layer = Physical transmission of data using 0’s and 1’s.
DHCP, DNS and WINS
What is DNS ?
It is used to resolve FQDN to IP address.
Types of Zone in DNS ?
Forward Lookup – it is used to resolve FQDN to IP
Reverse lookup – it is used to resolve IP to FQDN
Types of DNS Zone ?
- Primary Zone :
- Secondary Zone :
- AD integrated Zone :
- Stub Zone :
what is NSlookup ?
it is a tool used troubleshoot DNS related issues.
What is DHCP ?
DHCP is used to automatically provide IP address to client computers.
Explain DHCP 4 packets.
Discover = client sends request for IP.
Offer = DHCP server send and Offer with IP address.
Request = if clients accepts the IP it sends a request to DHCP.
Ack = DHCP server sends ack for the same.
What is client reservation in DHCP ?
To reserve a specific IP for a specific machine or host.
What is WINS ?
It is used to resolve NetBIOS Computer name to IP address.
Which port number DHCP uses?
DHCP uses UDP port number 67 and 68.
BASIC NETWORKING CONCEPTS
What is Web Server ?
Web server is a server or application server which host or stores websites.
Every web site should have a name like www.vision.com and IP address. Eg. IIS, Apache server, etc.
What is mail server ?
Mail server is a software which maintains user mailboxes. eg : Exchange server, Lotus domino, etc
What is mail client ?
A sofware used by client to access to mails stores on mail server. using mail client software you can send mail and receive mail. Eg : Microsoft Outlook, Outlook Express, Lotus notes, etc.
What is Proxy server ?
It is a software used for sharing of internet connection. Eg. Wingate, Winproxy, Analog proxy, etc.
Port numbers for various application and services
There are total 65536 ports available. Below are the list of some well-known ports.
LDAP : 389,Kerberos : 88,DNS : 53,SMTP : 25,POP3 : 110,Telnet : 23,NNTP : 119,IMAP : 143
RPC : 135,HTTP : 80,HTTPS / SSL : 443,FTP : 21
What is firewall ?
It is a software used to provide security to your network by not allowing unauthorized access to your Internal network from External users. Eg : PIX firewall, Checkpoint firewall, etc.
Which protocol is used by ADS for time sync. between PC’s?
SNTP (Simple network time protocol)
What is RPC protocol ?
RPC stands for Remote Procedure Call. It uses port number 135. RPC is an inter-process communication technique that allows client and server software to communicate.
What is COM ?
Component Object Model (COM) is Microsoft’s object-oriented programming model that defines how objects interact within a single application or between applications.
What is SNMP ?
SNMP stands for Simple Network Management Protocol). This protocol is used to monitor and manage network devices like Switches, Routers, Servers, etc. SNMP uses port UDP port number 161 and 162.
Basic Networking questions
What is the length of ipv6?
128 bit
Where is the hub specified in the OSI model?
Physical layer
Difference between TCP and UDP?
TCP
a) TCP is Transmission control protocol.
b) It is connection oriented.
c) Reliable
d) Uses checksum to detect errors.
UDP
a) UDP is user datagram protocol.
b) It is connectionless.
c) Non reliable.
d) No acknowledgement.
What is a gateway?
Gateway is a device that connects two dissimilar networks. It is in application layer.
Name the two routing protocols?
RIP & OSPF (intra domain routing protocol)
What is the advantage of OSPF protocol?
OSPF(open shortest path first) based on link state routing protocol. It handle routing efficiently and in timely manner.
7. What are the different layers in the OSI model?
Different layers of OSI model:
What is a firewall?
Firewall is a network that protects internet from unauthorized access. It is need for every computer system. proxy firewall is a type of firewall.
Difference between intra domain and inter domain routing protocol?
Routing within an autonomous system is referred as intra domain routing protocol and routing between an autonomous system is called as inter domain routing protocol.
Name the ports used by FTP protocol?
FTP is file transfer protocol. It copies file and transfer from one system to another port no is 20 for connection and port 21 is for data transfer.
Define Network?
A network is a collection of devices which are connected by means of physical media links or it is connection of two or more nodes in a recursive manner by a physical link.
What is a Link?
Link is a physical medium such as coaxial cable or optical fibre that connects two or more computers directly which form a network.
What is a node?
Links are physical medium that connects two or more computers directly and the computer it connects is called as nodes.
State the advantages of Distributed Processing?
The advantages are:-
a. Security/Encapsulation
b. Distributed database
c. Faster Problem solving
d. Security by means of redundancy
e. Collaborative Processing
Mention the factors by which a network performance is affected?
a. No. of Users
b. Transmission medium type
c. Hardware
d. Software
Name the factors that affect the reliability of the network?
a. Failure frequency
b. Network Recovery time after a failure
What are the key elements of protocols?
The key elements of protocols are as follows:-
a. Syntax
It refers to the format of the data, the order in which they are represented.
b. Semantics
It refers to the meaning of each section of bits.
c. Timing
Timing refers to: When data should be sent and how fast.
Mention the key design issues of a computer Network?
The Key design issues are as follows:-
a. Connectivity of the network
b. Cheap resource Sharing
c. Common Services will have support
d. Performance of the network
Define Bandwidth and Latency?
Performance of network is measured in Bandwidth called throughput and Latency called Delay. Network bandwidth is the number of bits which can be transmitted over the network over a certain period of time.
Latency refers to the time taken by a message to travel from one end of network to another. It is strictly measured in terms of time.
Describe the situation when a switch is said to be congested?
It is possible that a switch for an extended period of time can receives packets faster than the shared link can accommodate and stores in its memory, then the switch will eventually run out of buffer space, and some packets has to be dropped & is said to be congested state.
Describe semantic gap?
A useful channel includes both two things that is to understand the applications requirements and recognize underlying technology limitations.
The gap between what applications expects or desires and what the underlying technology can provide or give is called semantic gap.
Which layers are user support layers?
User support layers are as follows:-
a. Session layer
b. Presentation layer
c. Application layer
What is Error Detection? What are the methods?
During transmission data can get corrupted. In order to have a reliable communication errors must be deducted and corrected.
Error Detection uses the concept of redundancy by means of which it adds extra bits to detect errors at the destination.
The error detection methods are as follows:-
a. Vertical Redundancy Check
b. Longitudinal Redundancy Check
c. Cyclic Redundancy Check
d. Checksum
What are Data Words ?
Ans:- In block coding, message is divided into blocks, each of k bits, called data words. The same data word is always encoded as the same code word.
What is Framing?
Ans:- The work of framing in the data link layer is to separate a message from one source to a destination, or from other messages to other destinations, by adding a sender & destination address.
The destination address is the address of the packet where it has to go and the sender address helps the recipient acknowledge the receipt.
What is Error Control ?
Error detection and error correction is called as error control. If any frame is lost or damaged in transmission than the receiver inform it to that particular sender and ask to retransmit those frames by the sender. In the data link layer, error control refers primarily to methods of error detection and retransmission.
What is utility of sequence number in Reliable Transmission?
The protocol specifies that frames numbering has to be done using sequence numbers. A field is added to the data frame section in order to hold the sequence number of that frame.
As we want to minimize the frame size which will provide unambiguous communication. The sequence numbers can wrap around.
What is MAC address?
Media Access Control (MAC) layer is the device address in the network architecture. MAC address is unique and is usually stored in ROM on the network adapter card.
What is the difference between TFTP and FTP application layer protocols?
In order to obtain files from a remote host trivial file transfer protocol is used but it does not provide reliability or security. The File Transfer Protocol (FTP) is the standard mechanism which is by TCP / IP to copy a file from one host to another. TCP offer services that are reliable and secure. Two connections are established between the hosts, one for data transfer and another for control information.
What are major types of networks explain it?
Two major types-Server-based network: In this there is centralized control of network resources and it depends on server computers for security as well as network administration
Peer-to-peer network: In this the computers can act as both sharing resources servers as well as clients using the resources.






exllent questions …helpful to fresher..please provide more knowledge