We all know how industrial automation is progressing rapidly with IoT. It is a blend of networking and IT skills that has taken automation to a very new and great height. In that, one of the main systems which is used in very critical industries is SIS or safety instrumented systems. But where networking comes, there comes a cybersecurity threat also. It can hack and damage your system to a great extent if not prevented. Thankfully, international standards like ISA-99 help to prevent cybersecurity threats in such situations. In this post, we will see the top 5 cybersecurity threats to SIS systems and how ISA-99 prevents them.
How are SIS systems attacked by cybersecurity threats?
SIS stands for safety instrumented systems. It is a network of sensors, controllers, and control elements that mostly act in a closed loop or redundancy to check the safety of the process, and perform a response in case of a failure. The responses can range from shutting down a system safely to generating alarms or activating safety control elements that are present in the backup. They are designed or selected according to SIL or safety integrity level, which ranges from 1 to 4.
People think that SIS looks more like a hardwired and isolated system. It has fewer industrial communication protocols and cannot be threatened by cyber attackers, as it is not connected to the network. But, this is a very wrong perception. SIS also consists of controllers like PLC, which we discussed earlier. And PLCs have industrial communication protocols running on them in the network. Also, the sensors and field instruments used nowadays are mostly of smart or IoT-cloud-based type, which are connected to networks for advanced monitoring and diagnostics. To program them, the corresponding engineering tools or software are used, which is done by a PC or laptop connected to the network. Also, engineers mostly access these engineering workstations of a PC or a laptop remotely online and are thus exposed to wireless networks. That is why SIS too are threatened by cyberattacks and makes the process very risky to operate.
Top 5 Cybersecurity Threats to SIS Systems
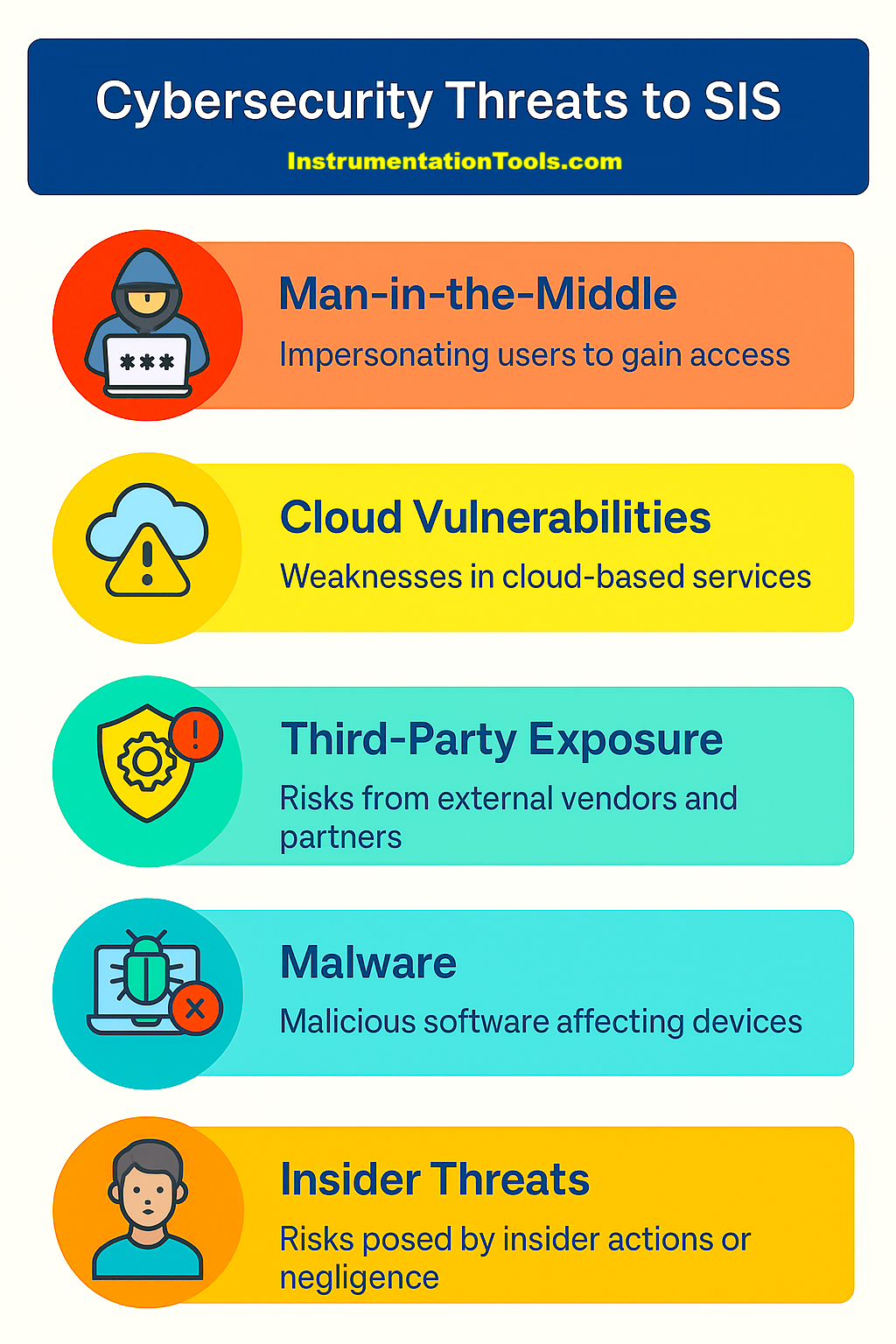
- An attacker impersonates a trusted user to gain access to SIS networks, often by intercepting communication between two parties, allowing them to manipulate or steal data.
- SIS components relying on cloud-based monitoring are exposed to threats such as misconfigured services, weak encryption, account hijacking, or shared technology vulnerabilities.
- Outsourced vendors and suppliers may unintentionally introduce threats. Improper handling of device data or access credentials can compromise the SIS network.
- Malicious code like viruses, trojans, or ransomware can be introduced via USB drives, engineering laptops, or LAN networks, compromising SIS logic, firmware, or devices.
- Disgruntled or careless employees may bypass cybersecurity practices, modify logic, disable protections, or share sensitive access, posing major internal risks.
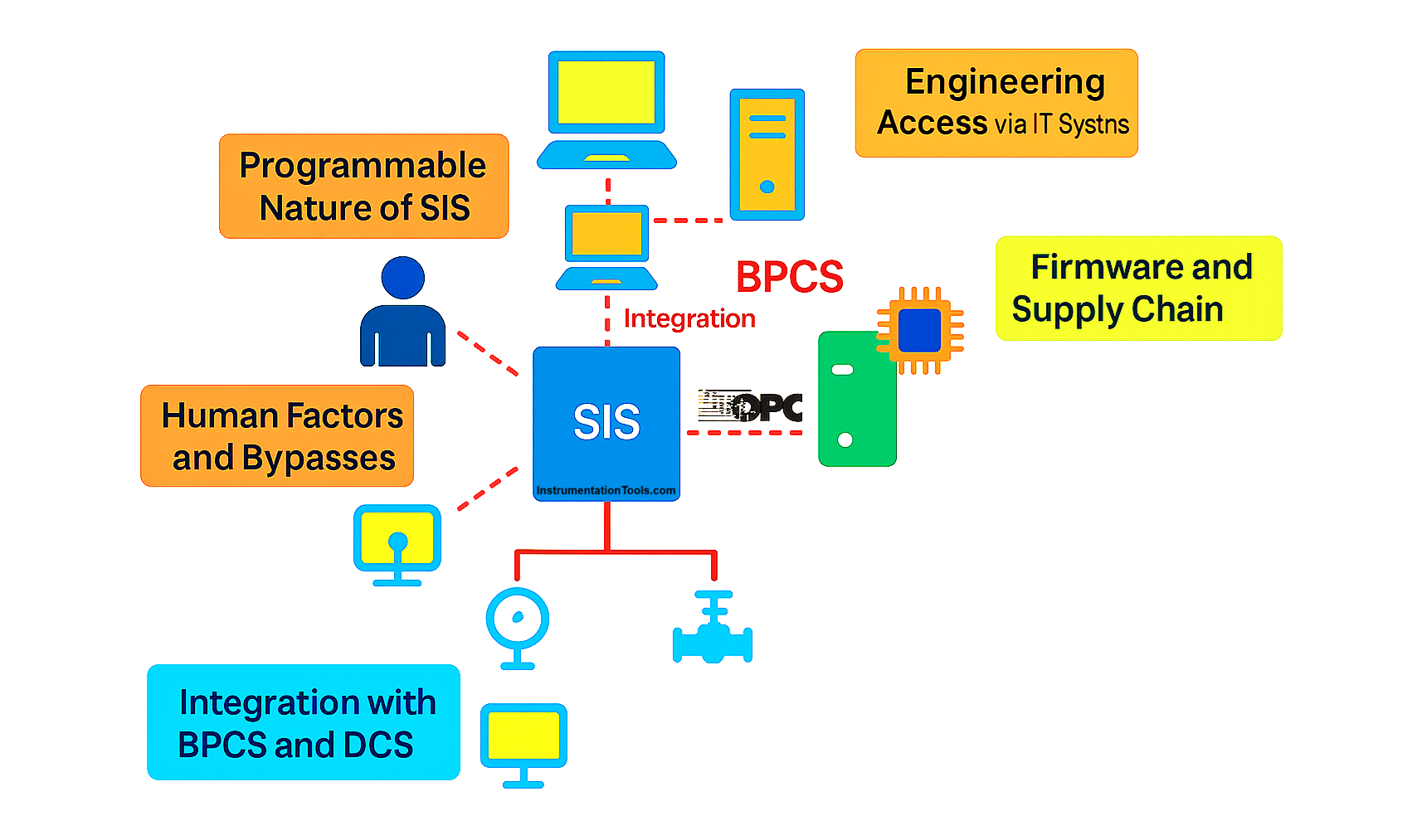
How ISA-99 Prevents Cybersecurity Threats on SIS Systems?
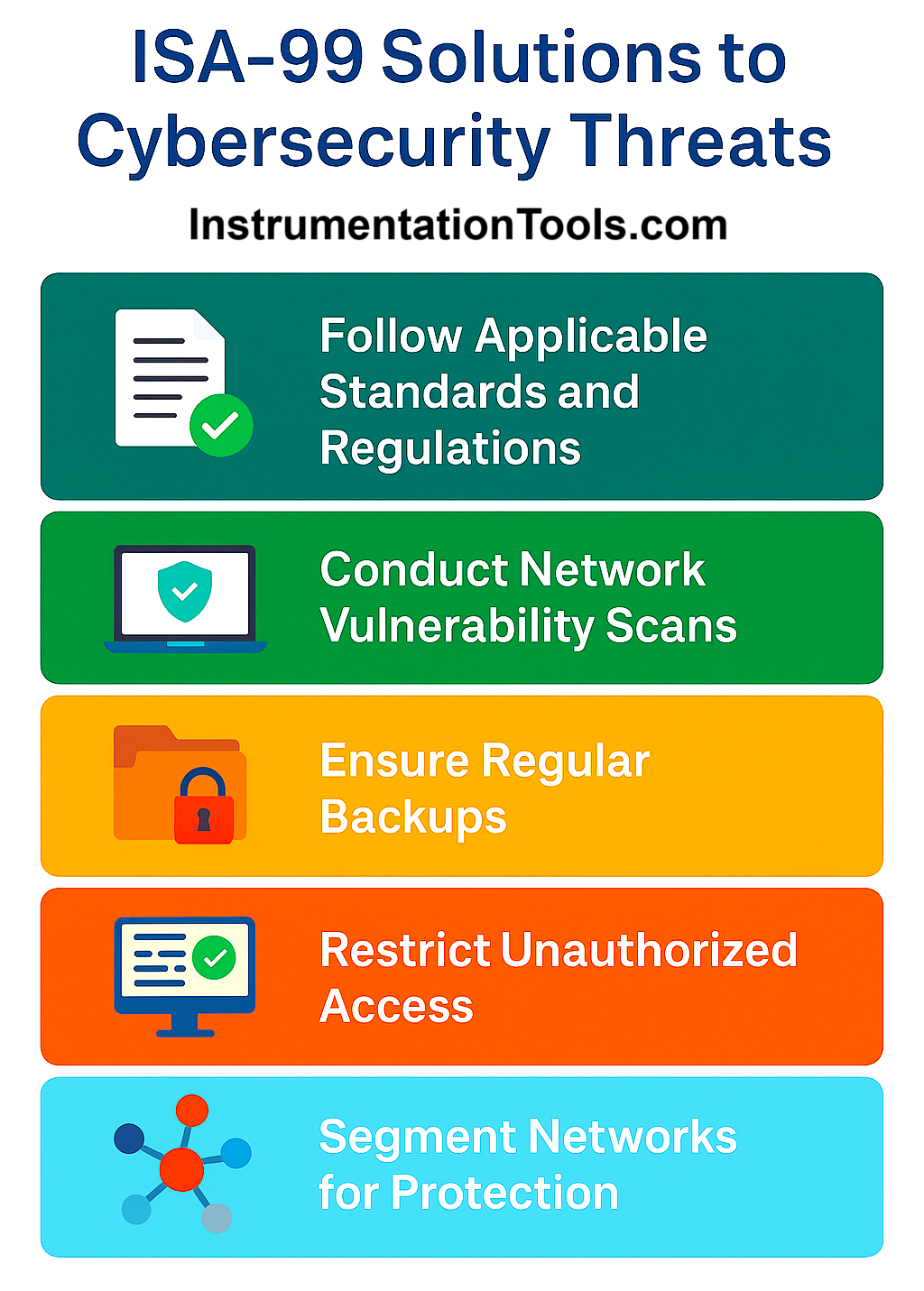
- Comply with the ISA-99/IEC 62443 standard and align plant operations with cybersecurity frameworks from the beginning.
- Implement zone and conduit architecture to isolate networks and contain threats within small, manageable areas.
- Assign security levels to each zone based on the system’s risk profile—from SL1 (casual) to SL4 (advanced persistent threats).
- Use firewalls, VPNs, data diodes, and authentication gateways in conduits to secure inter-zone communication.
- Conduct regular network vulnerability scans and implement access control policies.
- Enforce user privilege management through authentication, audit trails, and role-based access levels in SCADA/HMI systems.
- Ensure SIS firmware and software updates are validated, sourced securely, and deployed by authorized engineers.
- Avoid remote or USB-based access unless explicitly authorized and logged. Disable unnecessary ports on engineering workstations.
- Backup SIS configurations regularly and store securely with disaster recovery plans in place.
- Use safety PLCs with secure boot, memory protection, and tamper detection. Enable hardware key switches and disable unnecessary remote operations.
- Define, monitor, and log alarms and events precisely to detect suspicious activity early.
- Maintain a detailed SIS asset inventory including firmware versions, IP addresses, MAC IDs, vendor info, and update logs.
In this way, we saw the top 5 cybersecurity threats to SIS systems and how ISA-99 prevents them.
Read Next:
- SIS Design According to ISA-84
- ICS Cyber Security Training Course
- ISA-99 Network Segmentation in OT
- How to do Security of SCADA Systems?
- Right Industrial Automation Solution