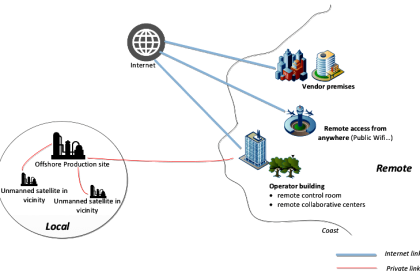
The remote connectivity to industrial automation systems can potentially enable unauthorized persons to access data, modify systems, introduce malware, or maliciously operate plant equipment. The consequences of such actions could lead to confidential data loss, commercial loss through production outages or in the worst case, safety incidents.
Remote Connectivity to Automation Systems
Most modern facilities, even if locally controlled and managed, will include the connection of local control systems to enterprise networks to enable data export for plant monitoring and financial accounting. Typically, this will be implemented using firewalls or data diodes that create a zone and conduit model to achieve appropriate network segmentation and restrict any direct connections between IACS and external systems.
An intermediate network or demilitarized zone (DMZ) network between enterprise and control system networks is typically used to prevent direct connections between the enterprise network and control system networks.
With correct implementation and management, office network-based systems and users can thus view data from control systems in a secure manner. The DMZ acts as a protection gateway between the safe zone (IACS network in the figure below) and the enterprise network.
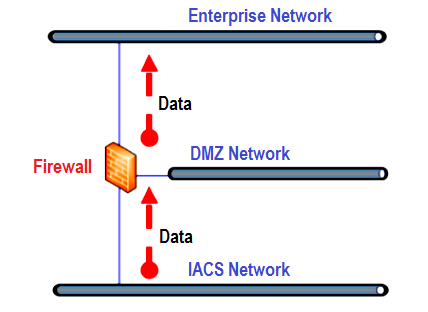
Figure 1: Overview of ‘Data Export’ architecture
Even with the simple ‘data export’ model above, significant security vulnerabilities can exist if networks and firewalls used to implement the required logical segregation are incorrectly designed or poorly managed.
Further, remote connections allow data to be transmitted beyond the site and the IACS networks. This allows the data to be stored, accessed, processed and replicated on a diverse set of non-IACS systems and networks. Thus, classifying and defining the policies around how and where the data can be processed is an important aspect.
The article focuses on the specific requirements related to remote access, but all IACS deployments require defense in depth against cyber threats. Several industry standards and guidelines (such as IEC 62443 series) cover the recommended protections and controls against cyber threats in detail. As such, these aspects are only briefly mentioned in this document.
‘Horizontal’ and ‘Vertical’ Remote Connectivity
Remote connectivity to control systems can be provisioned in two key ways, referred to here as ‘horizontal’ or ‘vertical’ connectivity.
The first is ‘horizontal’ connectivity – via extension of control system ‘zones’, whereby the local control network is extended to a remote location. Nominally, this provides an identical level 2 control system network access and functionality at the remote location to that at the local site or operational site.
The remote location retains the same security requirements as the IACS on the main site as they are fundamentally on the same security zone.
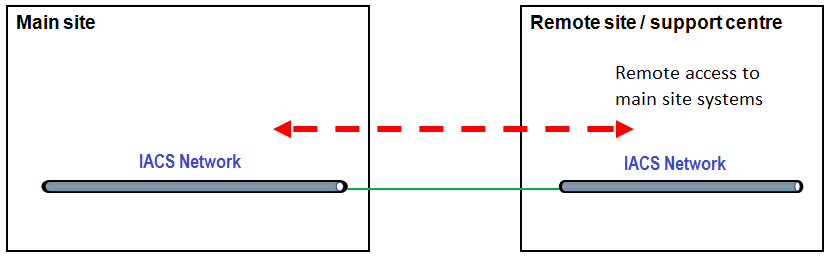
Figure 2: Overview of ‘horizontal’ remote connectivity
The second key way is ‘vertical’ connectivity – via the implementation of connectivity from a remote, higher level (such as office/IT-based) network to the local control network through a segregated and controlled ‘zone’ and ‘conduit’ architecture.
Access to control system networks is managed through strong authentication and network traffic controls (typically a firewall, or Intrusion Detection and Protection System (IDPS)).
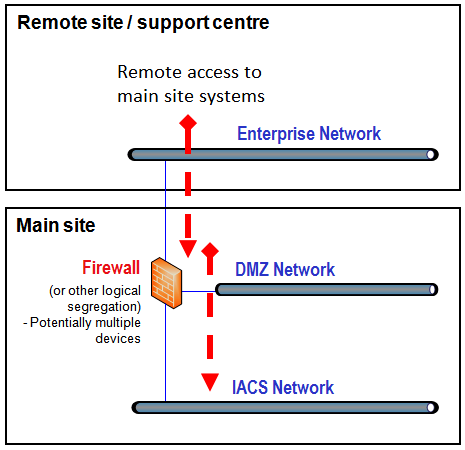
Figure 3: Overview of ‘vertical’ remote connectivity
‘Horizontal’ connectivity essentially maintains the remote functions within the IACS zone, thus relatively reducing the potential for external access as compared to vertical connectivity. However, it increases the entry points on the network, making them more distributed, and may create new vulnerabilities or common modes of failure, especially when the extension is not using dedicated network infrastructure.
‘Vertical’ connectivity, however, connects control systems to the enterprise network or external networks. This is sometimes achieved using third party networks. As all enterprise networks will have external internet connectivity and often run a managed service to allow inbound connections, ‘vertical’ connectivity typically introduces the threat of external access to control system networks.
In most facilities, some form of ‘vertical’ connectivity between control systems and enterprise networks as well as ‘horizontal’ connectivity is used, as they answer to a different operational need and use cases. Thus, in the provision of remote operating centers, it is common that hybrid architectures will be present.
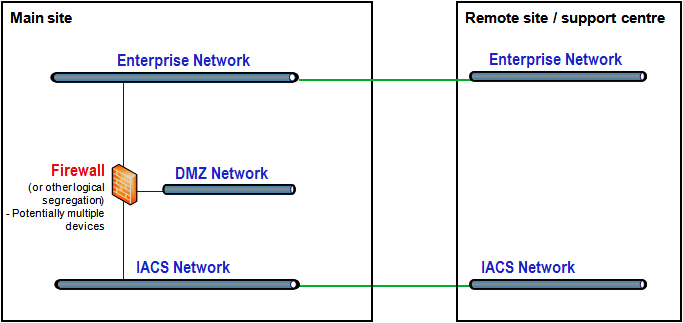
Figure 4: Overview of ‘hybrid’ architecture
‘Horizontal’ Remote Connectivity Considerations
The availability and reliability of communications between the remote and the local site are of importance to enable effective remote functions using the horizontal extension of IACS. These two factors are greatly influenced by the available telecom infrastructure (e.g., fiber, microwave or satellite technology), and the redundancy and resilience built into the telecommunication infrastructure.
‘Horizontal’ extension of IACS amplifies the threats inherent in a local facility and increases the potential for network-based attacks. The number of points of access is increased and the control of those access points becomes distributed and less visible. Remote access points are likely under the accountability of different persons or organizations to the local site and thus are more difficult to manage.
‘Horizontal’ extension often provides the connection to a remote control room, where physical access protection in the remote location should meet that of the local IACS zone and address any additional risks of unauthorized access.
Distancing the control functions from the site is also likely to increase the potential for operational risks and to create strong interdependencies between the local site and remote site.
‘Vertical’ Remote Connectivity Considerations
Where a remote operating center introduces ‘vertical’ remote connectivity, many new threat vectors are enabled. With ‘vertical’ remote connectivity, there is potential for anyone, operating from anywhere, to gain access to and operate local systems.
Key security goals include enforcing limits on who can access systems, what systems can be accessed and when, and enforcing role-specific user privileges.
Key controls to achieve this include:
- Secure network architecture
- Strong user authentication and authorization
- Remote Access Server security
- The remote host or device security
- Security monitoring
Guidance on effectively applying these security measures are widely available in industry standards and recommended practices.
Source: International Association of Oil & Gas Producers
Acknowledgments: IOGP Instrumentation and Automation Standards Subcommittee (IASSC) Remote Operating Centres Task Force.
Read Next:
- Cyber Security Glossary
- Security of SCADA Systems
- What is Energize to Safe Loop?
- Setpoints and Alarms in DCS
- PID Controller Analysis