ICS controls the physical world and IT systems manage data. ICS has many characteristics that differ from traditional IT systems, including different risks and priorities. Some of these include significant risk to the health and safety of human lives, serious damage to the environment, and financial issues such as production losses, and a negative impact on a nation’s economy.
ICS have different performance and reliability requirements, and also use operating systems and applications that may be considered unconventional in a typical IT network environment. Security protections must be implemented in a way that maintains system integrity during normal operations as well as during times of cyber attack.
Initially, ICS had little resemblance to IT systems in that ICS were isolated systems running proprietary control protocols using specialized hardware and software. Widely available, low-cost Ethernet and Internet Protocol (IP) devices are now replacing the older proprietary technologies, which increases the possibility of cybersecurity vulnerabilities and incidents.
As ICS are adopting IT solutions to promote corporate connectivity and remote access capabilities, and are being designed and implemented using industry-standard computers, operating systems (OS) and network protocols, they are starting to resemble IT systems. This integration supports new IT capabilities, but it provides significantly less isolation for ICS from the outside world than predecessor systems, creating a greater need to secure these systems.
While security solutions have been designed to deal with these security issues in typical IT systems, special precautions must be taken when introducing these same solutions to ICS environments. In some cases, new security solutions are needed that are tailored to the ICS environment.
The environments in which ICS and IT systems operate are constantly changing. The environments of operation include, but are not limited to: the threat space; vulnerabilities; missions/business functions; mission/business processes; enterprise and information security architectures; information technologies; personnel; facilities; supply chain relationships; organizational governance/culture; procurement/acquisition processes; organizational policies/procedures; organizational assumptions, constraints, risk tolerance, and priorities/trade-offs).
The following lists some special considerations when considering security for ICS:
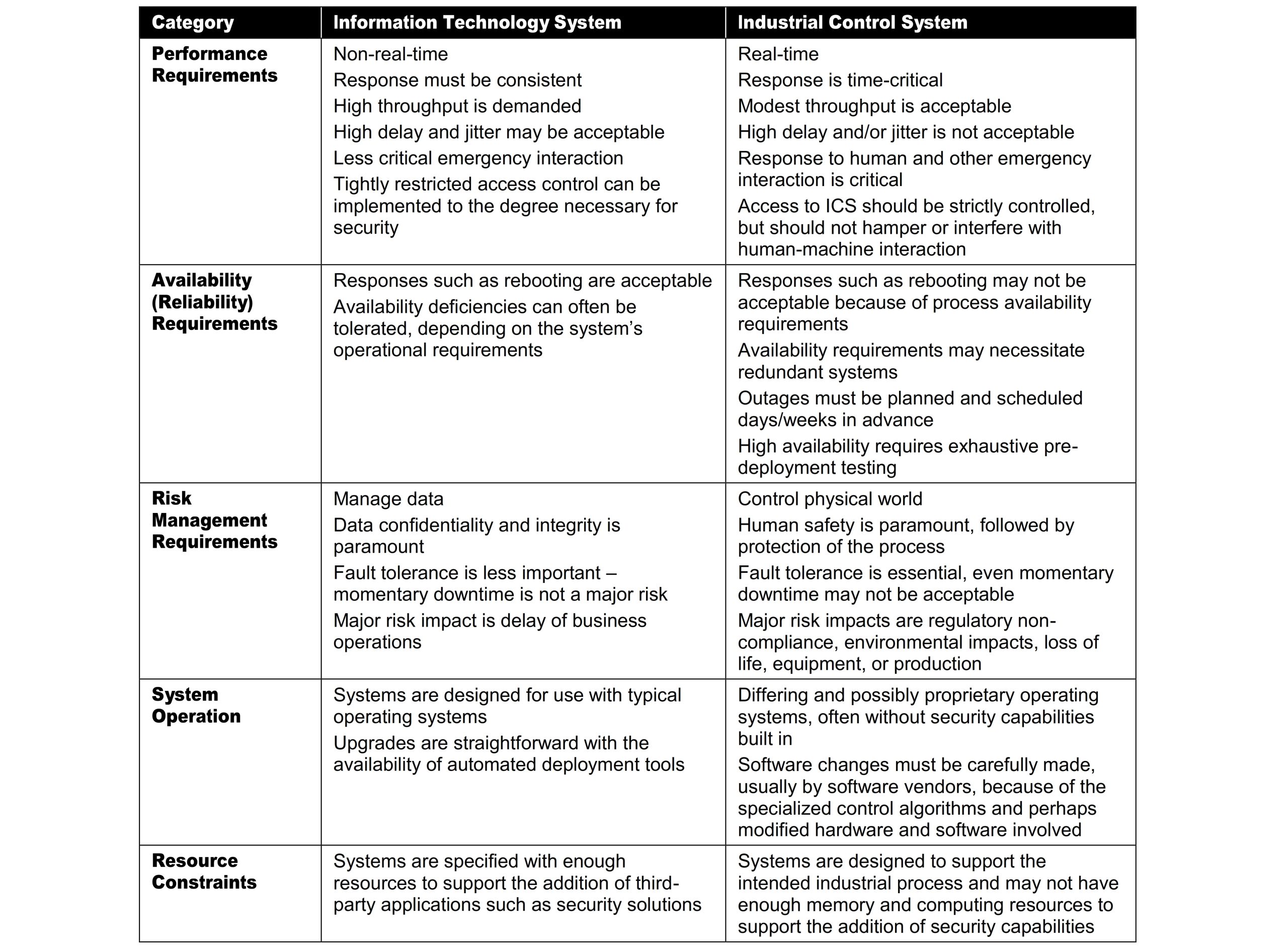
Timeliness and Performance Requirements
ICS is generally time-critical, with the criterion for acceptable levels of delay and jitter dictated by the individual installation. Some systems require reliable, deterministic responses. High throughput is typically not essential to ICS.
In contrast, IT systems typically require high throughput, and they can typically withstand some level of delay and jitter. For some ICS, automated response time or system response to human interaction is very critical.
Some ICS are built on real-time operating systems (RTOS), where real-time refers to timeliness requirements. The units of real-time are very application dependent and must be explicitly stated.
Availability Requirements
Many ICS processes are continuous in nature. Unexpected outages of systems that control industrial processes are not acceptable. Outages often must be planned and scheduled days or weeks in advance. Exhaustive pre-deployment testing is essential to ensure high availability (i.e., reliability) for the ICS.
Control systems often cannot be easily stopped and started without affecting production. In some cases, the products being produced or equipment being used is more important than the information being relayed.
Therefore, the use of typical IT strategies such as rebooting a component, are usually not acceptable solutions due to the adverse impact on the requirements for high availability, reliability, and maintainability of the ICS. Some ICS employs redundant components, often running in parallel, to provide continuity when primary components are unavailable.
Risk Management Requirements
In a typical IT system, data confidentiality and integrity are typically the primary concerns. For an ICS, human safety and fault tolerance to prevent loss of life or endangerment of public health or confidence, regulatory compliance, loss of equipment, loss of intellectual property, or lost or damaged products are the primary concerns.
The personnel responsible for operating, securing, and maintaining ICS must understand the important link between safety and security. Any security measure that impairs safety is unacceptable.
Physical Effects
ICS field devices (e.g., PLC, operator station, DCS controller) are directly responsible for controlling physical processes.
ICS can have very complex interactions with physical processes and consequences in the ICS domain that can manifest in physical events. Understanding these potential physical effects often requires communication between experts in control systems and in the particular physical domain.
System Operation
ICS operating systems (OS) and control networks are often quite different from IT counterparts, requiring different skill sets, experience, and levels of expertise.
Control networks are typically managed by control engineers, not IT personnel. Assumptions that differences are not significant can have disastrous consequences on system operations.
Resource Constraints
ICS and their real-time OSs are often resource-constrained systems that do not include typical contemporary IT security capabilities. Legacy systems are often lacking resources common in modern IT systems.
Many systems may not have desired features including encryption capabilities, error logging, and password protection. Indiscriminate use of IT security practices in ICS may cause availability and timing disruptions.
There may not be computing resources available on ICS components to retrofit these systems with current security capabilities. Adding resources or features may not be possible.
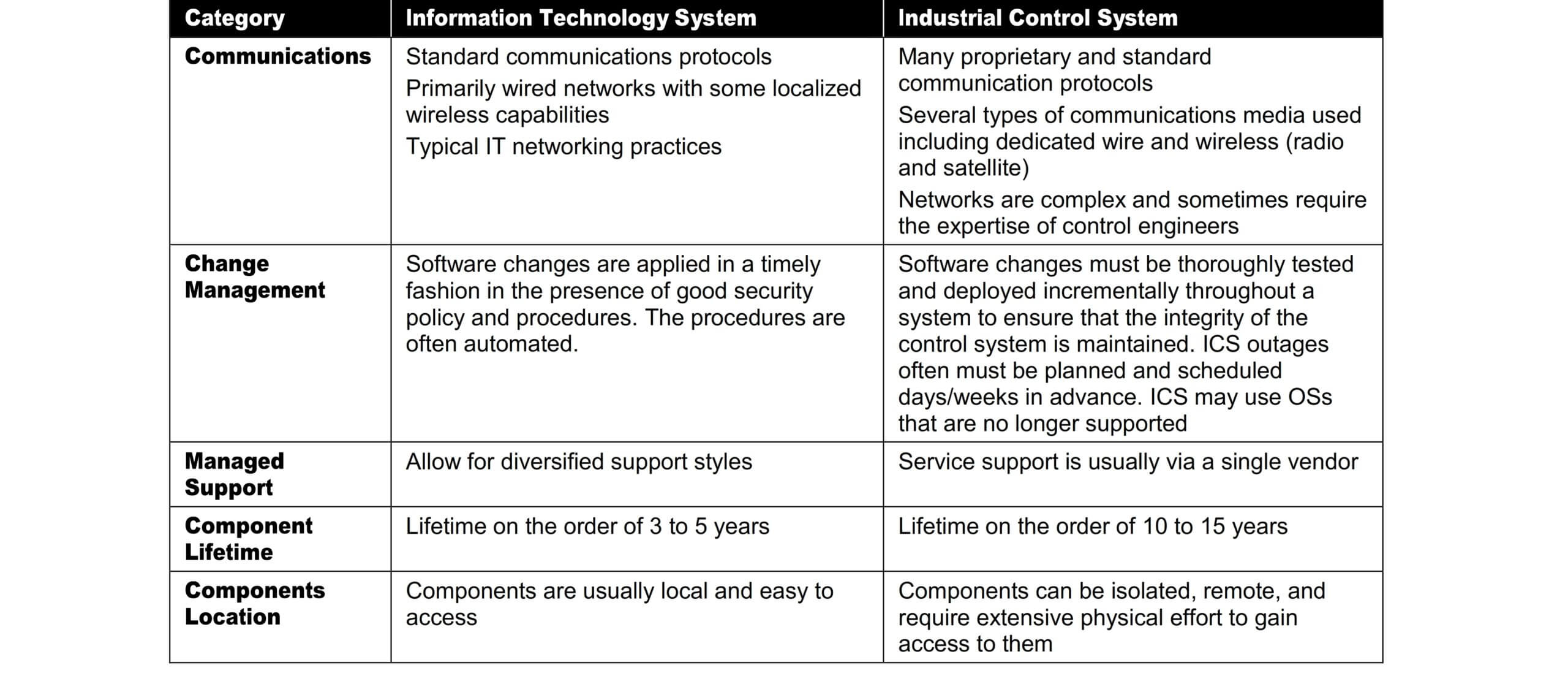
Communications
Communication protocols and media used by ICS environments for field device control and intra-processor communication are typically different from most IT environments and may be proprietary.
Change Management
Change management is paramount to maintaining the integrity of both IT and control systems. Unpatched software represents one of the greatest vulnerabilities to a system. Software updates on IT systems, including security patches, are typically applied in a timely fashion based on appropriate security policy and procedures.
In addition, these procedures are often automated using server-based tools. Software updates on ICS cannot always be implemented on a timely basis. These updates need to be thoroughly tested by both the vendor of the industrial control application and the end-user of the application before being implemented.
Additionally, the ICS owner must plan and schedule ICS outages days/weeks in advance. The ICS may also require revalidation as part of the update process. Another issue is that many ICS utilizes older versions of operating systems that are no longer supported by the vendor. Consequently, available patches may not be applicable.
Change management is also applicable to hardware and firmware. The change management process, when applied to ICS, requires careful assessment by ICS experts (e.g., control engineers) working in conjunction with security and IT personnel.
Managed Support
Typical IT systems allow for diversified support styles, perhaps supporting disparate but interconnected technology architectures. For ICS, service support is sometimes via a single vendor, which may not have a diversified and interoperable support solution from another vendor.
In some instances, third-party security solutions are not allowed due to ICS vendor license and service agreements, and loss of service support can occur if third-party applications are installed without vendor acknowledgment or approval.
Component Lifetime
Typical IT components have a lifetime on the order of 3 to 5 years, with brevity due to the quick evolution of technology.
For ICS where technology has been developed in many cases for very specific use and implementation, the lifetime of the deployed technology is often in the order of 10 to 15 years and sometimes longer.
Component Location
Most IT components and some ICS are located in the business and commercial facilities physically accessible by local transportation. Remote locations may be utilized for backup facilities. Distributed ICS components may be isolated, remote, and require extensive transportation effort to reach. The component location also needs to consider the necessary physical and environmental security measures.
The table summarizes some of the typical differences between IT systems and ICS.
In summary, the operational and risk differences between ICS and IT systems create the need for increased sophistication in applying cybersecurity and operational strategies.
A cross-functional team of control engineers, control system operators, and IT security professionals needs to work closely to understand the possible implications of the installation, operation, and maintenance of security solutions in conjunction with control system operation.
IT professionals working with ICS need to understand the reliability impacts of information security technologies before deployment. Some of the OSs and applications running on ICS may not operate correctly with commercial-off-the-shelf (COTS) IT cybersecurity solutions because of specialized ICS environment architectures.
Reference: National Institute of Standards and Technology Special Publication 800-82, Revision
If you liked this article, then please subscribe to our YouTube Channel for PLC and SCADA video tutorials.
You can also follow us on Facebook and Twitter to receive daily updates.
Read Next:
- Instrumentation Design
- Types of System Architecture
- Automation and Control System
- System Reference Model
- System Remote Connectivity