Industrial automation today largely revolves around IT and OT, which is nothing but the convergence of IoT or Industry 4.0. Though IT is still stringent and hardened by network engineers, issues are mostly faced when working with lower levels of OT, or the PLC/SCADA level. If such networks are not stringent in operation, then the risks of cybersecurity are increased to a large extent, which can hamper the system’s performance. So, it is required to segment the OT networks into groups, which is guided by ISA-99 standards. In this post, we will see how to segment OT networks using ISA-99 guidelines.
Importance of Cybersecurity in Operational Technology
Nowadays, most of the lower-level automation systems are integrated with Ethernet layer hardware, due to the flexibility of network integration. But, the network configuration in these systems is mostly not configured keeping cybersecurity in mind, which makes it vulnerable to hacks and security data loss. Anyone could access the network system, make changes, create network congestion, and increase disruption. This will make the process perform badly and hamper the business. So, to avoid such intrusions, cybersecurity is very important in the OT layers of the process.
What Role Does ISA-99 Play in Cybersecurity?

Now, we will next understand the role of the ISA-99 standard in cybersecurity. ISA-99, now recognised as IEC 62443, is an international standard body for working on industrial control network security. It covers a wide variety of topics like:
- Studying the existing network layer architecture with security in it
- Aligning with the security hazard potentials
- Splitting the network into groups and segments
- Working closely on strict security methods like authentication and system integrity
- Understanding the role of each network security component
- Defining security levels based on threats
The standard is thus responsible for guiding the industrial processes on how to securely work with their IT and OT layers of automation. This prevents cybersecurity issues to a great extent.
What is the Need for Network Segmentation in an OT System?
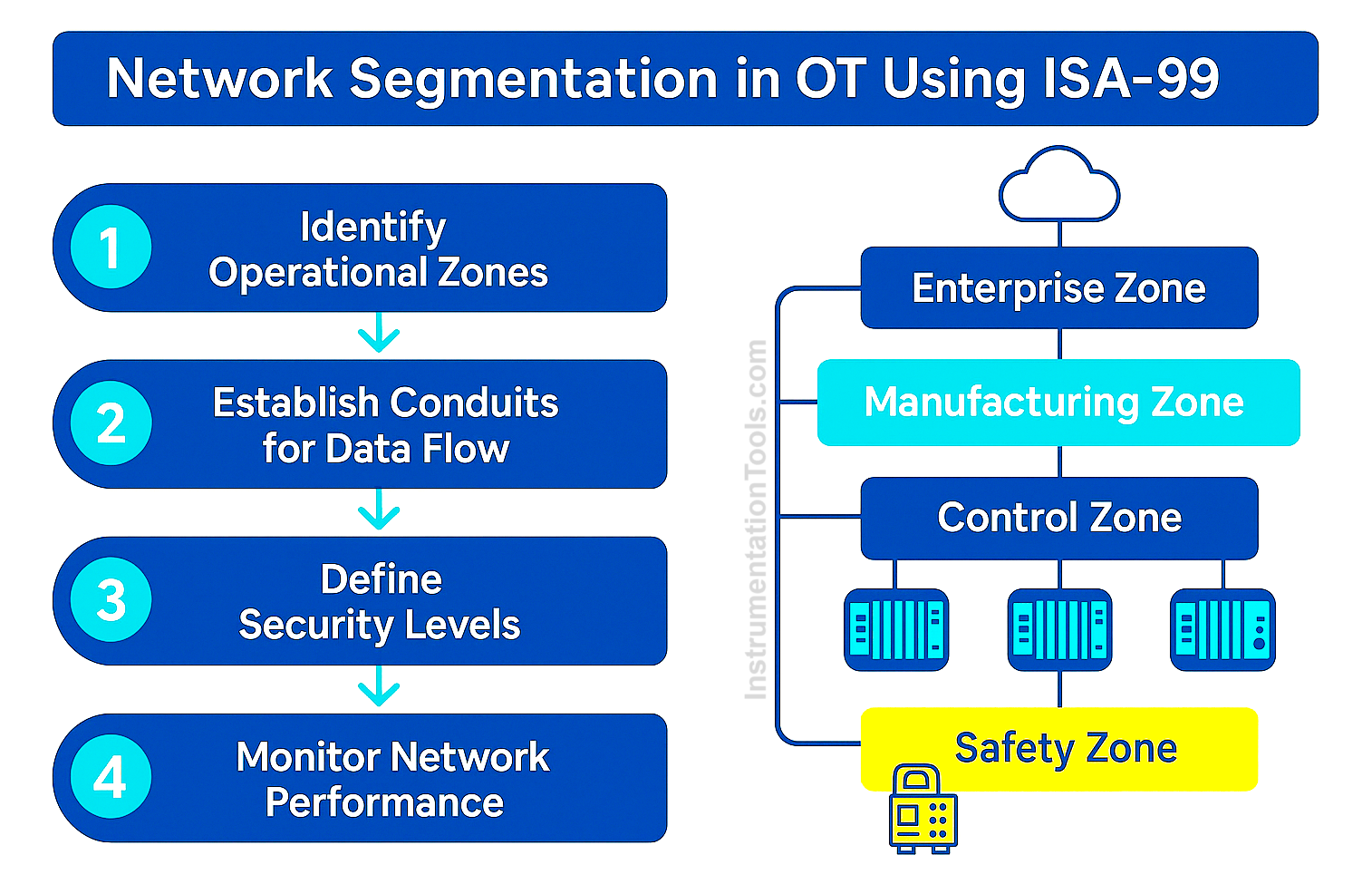
As per ISA-99 guidelines, there is an option where you can break your network into various small networks. This is called network segmentation. This feature plays a very important role in cybersecurity. By splitting your single network into multiple small groups of networks, each network will remain isolated from the others. Each network will have its own identity or address, function, and security levels to access. Due to this, you can easily divide your plant network into multiple networks for ease of operation and flexibility.
In terms of the standard, this function is identified as zones and conduits. Let us check more deeply how to segment the networks in OT:
1. First, identify groups of PLCs and SCADA systems that have similar functions and criticality. Based on that, make groups of such devices. This will give a clear identity of the segments to be networked differently.
2. This activity completes your action in the zones. A zone is a group of physical and logical devices sharing the same purpose of operation. Each zone should reflect a logical grouping based on criticality and function.
3. A conduit is a communication path that connects different zones. Conduits can be implemented using firewalls, VPNs, or data diodes. The conduit ensures that data flow between zones is secure and only authorized access is allowed. Each conduit must be configured appropriately based on the data flow needs and security requirements.
4. Once zones and conduits are identified, assign roles to each:
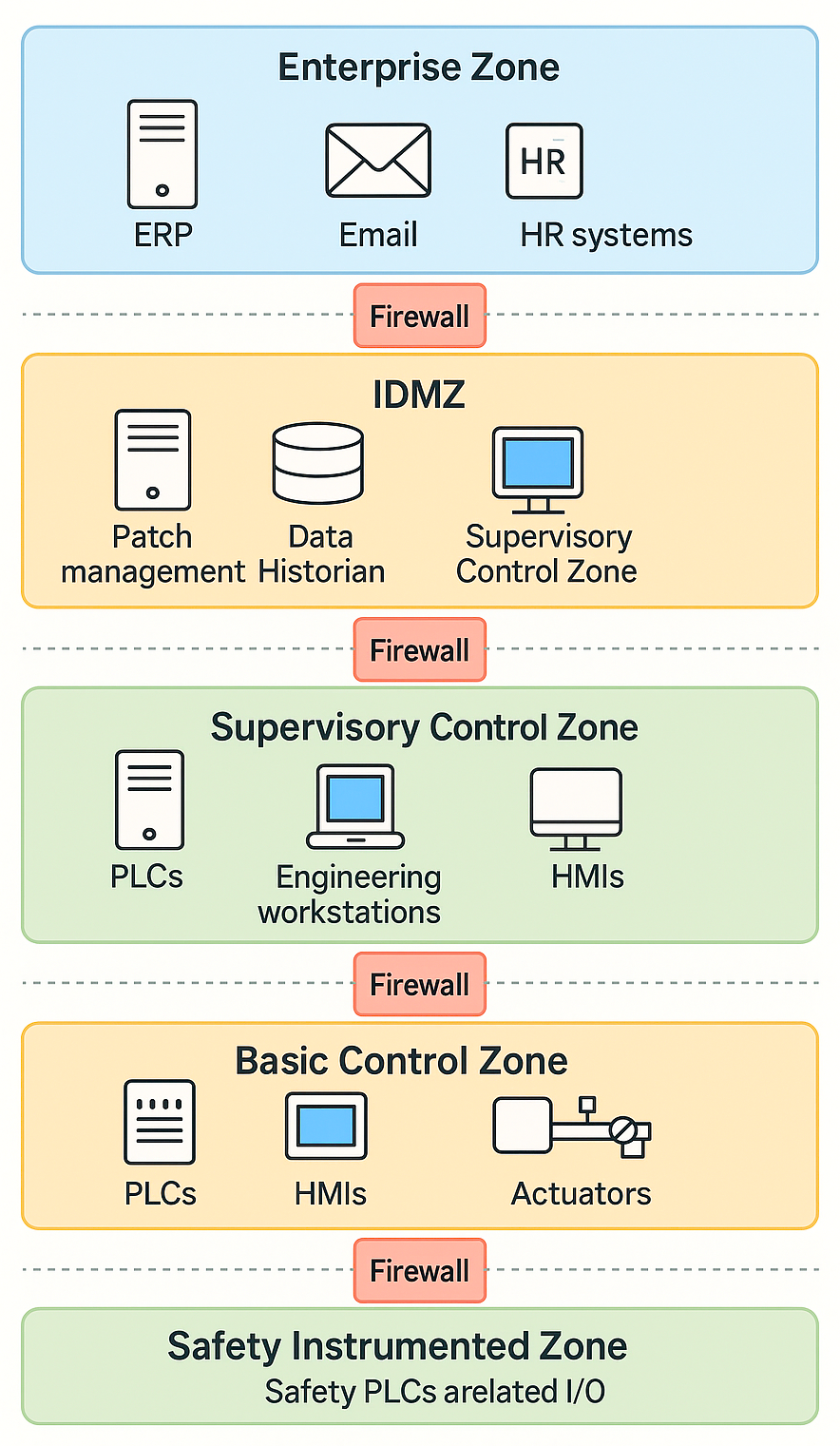
- Enterprise Zone (Business Network, ERP, MES)
- Supervision Zone (SCADA, HMI systems)
- Control Zone (PLC, RTU, DCS systems)
- Safety Instrumented Zone (SIS controllers, sensors, actuators)
Understand the industrial Ethernet protocols (Modbus TCP/IP, Profinet, Ethernet/IP, etc.) and their compatibility in each segment.
5. Define each zone with a security level from SL1 to SL4:
- SL1: Protection against casual violations
- SL2: Protection against intentional violations using simple means
- SL3: Protection against sophisticated attackers
- SL4: Protection against highly sophisticated and targeted attacks
Assign the security level based on a thorough risk assessment.
Example Layout
Refer to the image below for a conceptual diagram of OT network segmentation. The diagram will typically illustrate hierarchical segmentation starting from the Enterprise Zone at the top to the SIS Zone at the bottom, showing secured conduits between zones according to ISA-99.
Conclusion
In this way, we saw how to segment OT networks using ISA-99 guidelines. Implementing zones and conduits as per ISA-99 not only improves cybersecurity but also provides a structured approach to managing industrial network infrastructure effectively.
Read Next:
- Cybersecurity in PLC Systems
- What is the HIPPS System?
- SIS Design According to ISA-84
- Safety PLC Bypass and Impairment
- ICS Cyber Security Training Course