Identify critical alerts and program a trap for those alerts. Set the trap to monitor the trigger conditions and the alert state for any deviation.
| Security Objective | Target Group |
| Monitoring | Integration / Maintenance Service Provider |
Identify PLC Critical Alerts
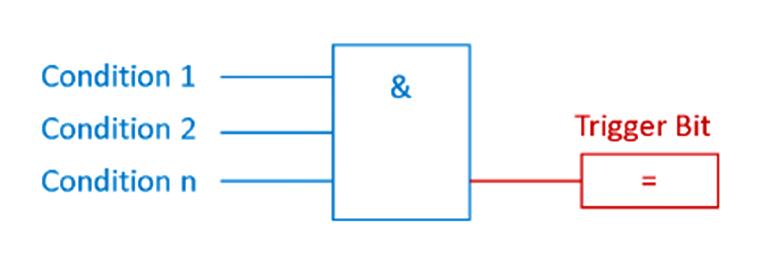
In most cases, alert-states are boolean (True, False) and triggered by certain conditions as displayed below.
For example, the trigger bit for the alert ‘overpressure’ becomes TRUE, if Condition 1 ‘pressure switch 1’, Condition 2 ‘pressure sensor value over critical threshold’, through n., are TRUE.
To masquerade an attack, an adversary could suppress the alert trigger bit and cause a false negative.
A trap for false negatives monitors the conditions for the trigger bit and the negated trigger bit itself. With this simple setup, a false negative is detected. See the following picture:
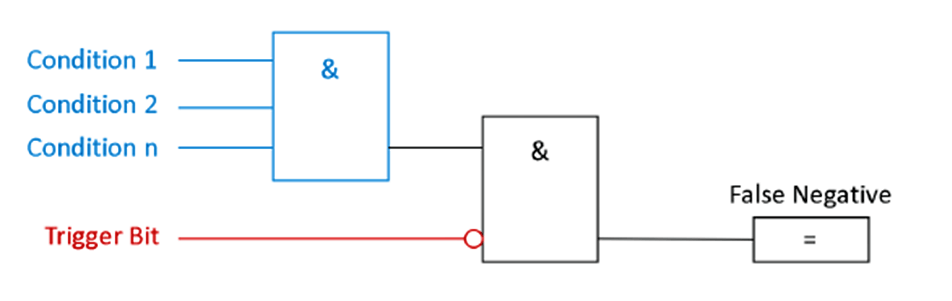
In other cases, an adversary could deliberately cause false positives, to wear down the process operator’s attention.
In the same manner of the false negative trap, false positives can also be detected by monitoring the alert trigger bit and if the trigger conditions are met. If the conditions are NOT met, but the trigger bit is active, a false positive is detected: See the following picture:
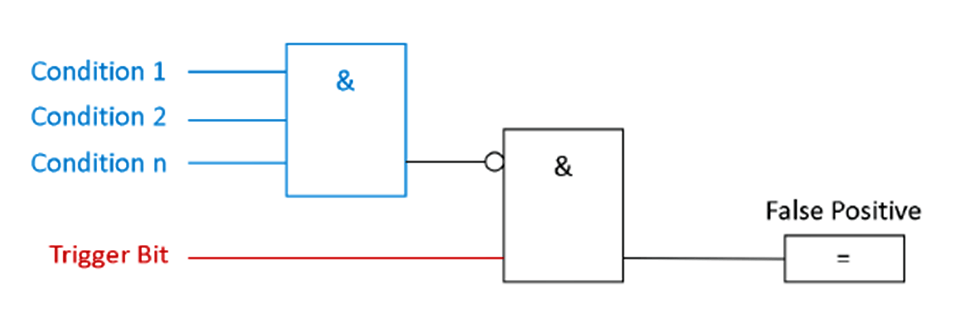
Example 1
Siemens offers in their Siemens S7-1200/1500 Products a Webserver with a wide range of functions, for example, display of the PLC-State, cycle time, or scope records.
It also has the option to view and modify data tables and variables. The access rights to the Webserver can be modified in the PLC-Hardware Settings.
In case of mis-configured access rights, an adversary could gain access to the PLC Variables and Datablocks. To create a false positive, the adversary selects an alert trigger bit and alters the state.
Example 2
In the Triton/Trisys/HatMan attack, rogue code suppressed alert states.
Example 3
A bus-injection attack could send a false positive alert to a high-level SCADA client.
Why?
| Beneficial for…? | Why? |
| Security | Mitigates false negative or false positives of critical alert messages caused by an adversary obfuscating their attack (i.e., rogue code, bus injection, tampering with accessible PLC state tables on unsecured web servers). |
| Reliability | / |
| Maintenance | / |
References
| Standard/framework | Mapping |
| MITRE ATT&CK ICS | Tactic : TA009 – Inhibit Response Function Technique: T0878 – Alarm Suppression |
| ISA 62443-3-3 | SR 3.5: Input Validation |
| ISA 62443-4-2 | CR 3.5: Input Validation |
| ISA 62443-4-1 | SI-1: Security implementation review |
| MITRE CWE | CWE-754: Improper Check for Unusual or Exceptional Conditions |
Source: PLC Security