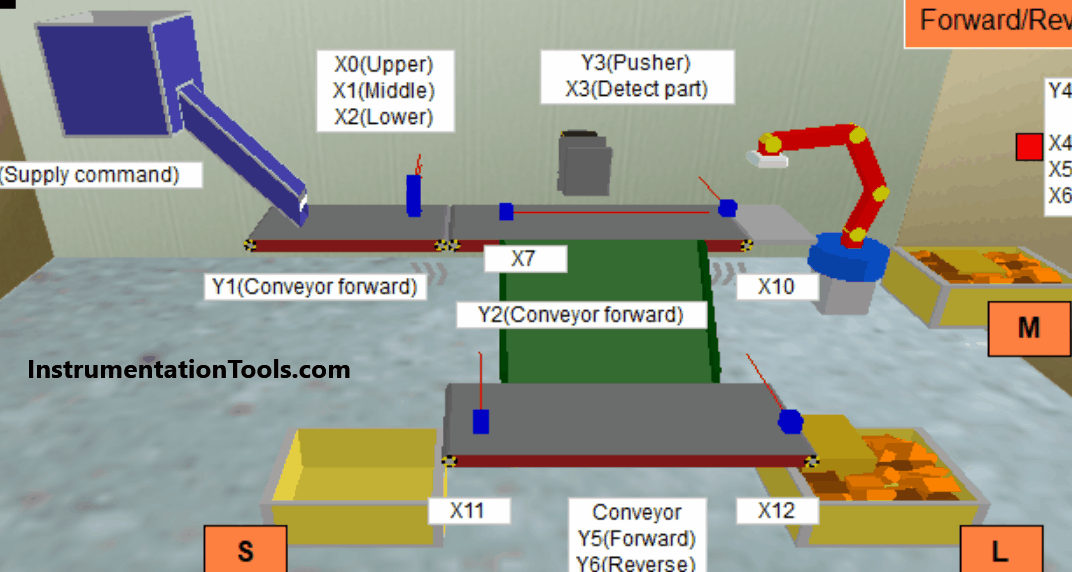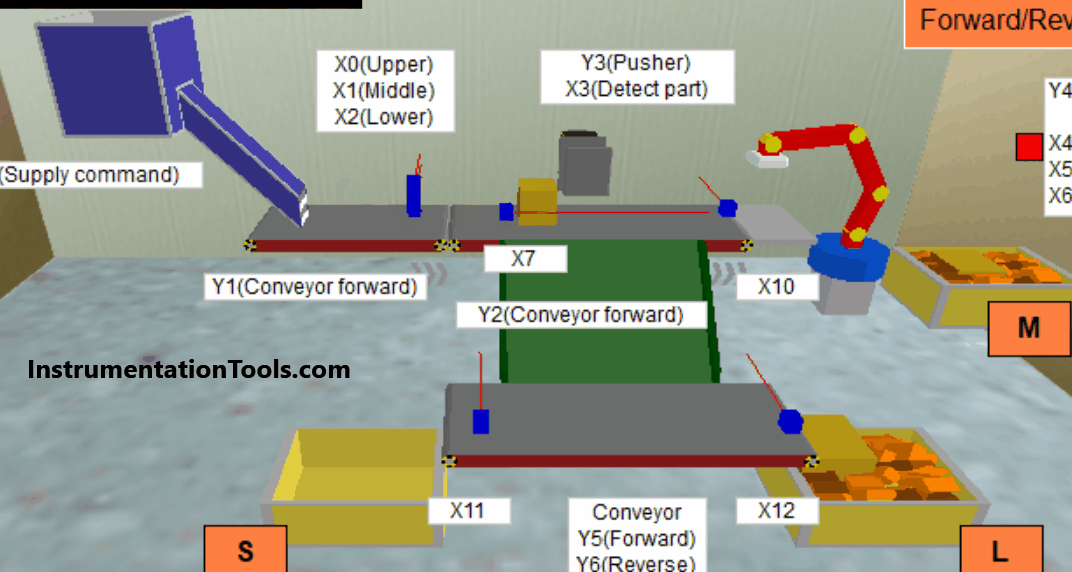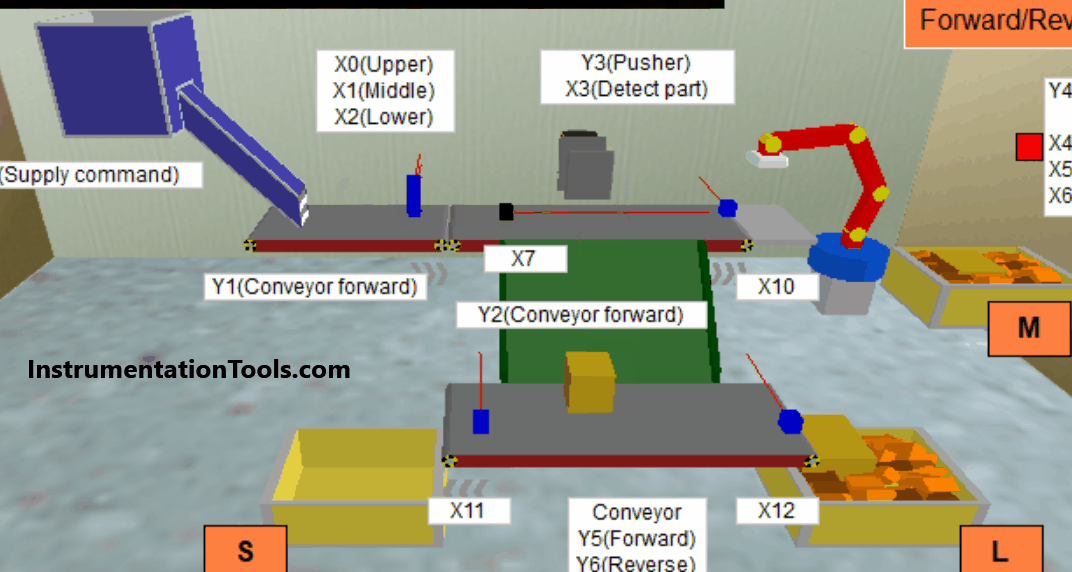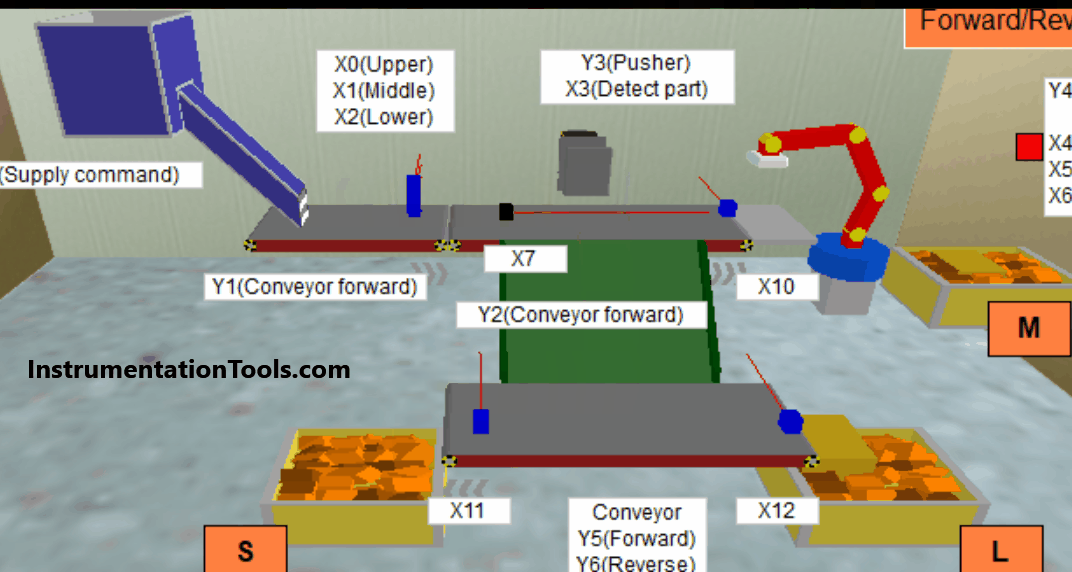
When you are working in a computer network system, you have to deal mostly with two types of addresses – IP (internet protocol) and MAC (media access control). These two are the objects which must be understood properly for working in a network.
Before establishing the connection between two devices, a device first knows the IP address. But to find the MAC address, a separate protocol is used. This is called address resolution protocol (ARP). In this post, we will see the concept of ARP in networking.
Address Resolution Protocol

First of all, let us understand the basics. Networking works on the basis of the OSI layer model. It consists of seven layers in the following sequence from start to end – physical, data link, network, transport, session, presentation, and application.
Related to our topic, MAC addresses work on the data link layer and IP addresses work on the network layer. Whenever a device on a network wants to communicate with another device, it must know two of its things – IP address and MAC address.
The IP address is 32-bit long and identifies the network address of the device; for example – 192.168.10.30. The MAC address is 48-bit long and identifies the physical address of the device; for example – A5:23:97:76:20:65. The IP address can be obtained either manually entering or automatically by DHCP or BOOTP. The MAC address is fixed for a device and does not change.
Now, when a device wants to communicate in a network, its request starts from the application layer to the physical layer and goes to the other device from the physical layer to the application layer as a response. Coming back to our terms, both devices will have their IP addresses. But, to communicate on the network, it must know their MAC addresses. So, the requesting device will send its message along with the IP address on the network with a broadcast asking who the MAC ID belongs to. The corresponding MAC ID device will respond by saying it is its ID.
Due to this, the MAC ID of that device will now be stored along with its IP address in a memory table. This table is known as the ARP cache. This cache is responsible for holding all the network values in a device. All these exchanges are thus possible through a protocol named ARP.
Once the device ID has been saved, the ARP will now not again send requests for device ID recognition. It will send a request for a new device in the network and will help identify it. Without ARP, the device will only have the network addresses of the devices in the network, but no MAC addresses. This will not help to establish communication.
Types of ARP
The main types of ARP are proxy ARP and Reverse ARP.
Proxy ARP
You must have heard how some students in a college mark the attendance of their colleagues on behalf of their absence. It means they are doing proxy. Similarly, proxy ARP here means that a third-party device is representing itself as the actual device and is helping the ARP cache in getting the desired addresses.
A simple example can be a router. A proxy router is present in the network which communicates with devices from other subnet and IP addresses. When it receives a request from a different network device, it will act as the middleman and share all the information of the MAC address required. Once established, that corresponding device of the router network will directly link with the device that asked for the request.
Reverse ARP
The “Reverse ARP” is the reverse working of ARP as the name suggests. As the ARP is used to find MAC addresses from an IP address, this ARP is used to find IP addresses from the MAC address.
A reverse ARP server is present in the network containing the MAC addresses of the devices. When a replacement device comes up in the network, there are chances that it will not know its IP address. So, it will send a broadcast message containing its MAC address.
The server will receive the request and match it in its ARP cache memory containing MAC to IP addresses. If it finds the matching one, it will know that the device has been replaced and is new in the network with the same configuration. So, it will send the receiving broadcast message back to the sender containing its IP address.
Important terms related to ARP:
ARP Spoofing
“ARP spoofing” is a type of cyber attack where the hacker will send fake broadcast messages to the network requesting the receiver’s MAC address. It will have the same IP address and it will then get the response from the victim’s IP address by matching its MAC address from the ARP cache. This will expose the victim’s data to the hacker’s computer.
ARP cache timeout
The “ARP cache timeout” is the time that defines when the MAC address can reside in the ARP cache. After this, the MAC address will be erased from the memory and ARP will again send a request for that.
ARP cache
ARP cache is a memory that is used to store the mapping of IP addresses to the corresponding MAC addresses. It is then used for establishing communication between devices.