Assign designated register blocks for specific functions in order to validate data, avoid buffer overflows and block unauthorized external writes to protect controller data.
| Security Objective | Target Group |
| The integrity of PLC variables | Product Supplier Integration / Maintenance Service Provider |
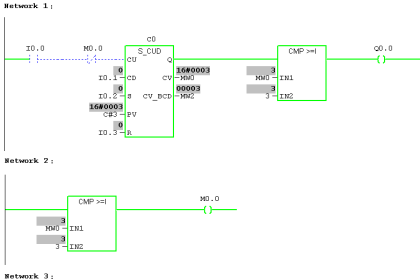
Assign Register blocks by Function in PLC
Temporary memory, also known as scratch-pad memory, is an easily exploitable area of memory if this practice is not followed. e.g., simply writing to a “Modbus” register that is out of bounds could lead to overwriting memory registers used for temporary calculations.
Generally, register memory can be accessed by other devices across the PLC network for read and write operations. Some registers could be read by an HMI, and others could be written by a SCADA system, etc.
Having specific register arrays for a certain application also makes it easier (in the controller or an external firewall is used) to configure Read-only access from another device/HMI.
Examples of functions for which designated register blocks make sense are:
- reading
- writing (from HMI / Controller / other external device)
- validating writes
- calculations
Ensuring external writes to allowable registers also helps in avoiding main memory reset errors either due to out-of-bound execution or malicious attempts.
These designated register blocks can be used as buffers for I/O, timer, and counter writes by validating that the buffer is completely written (does not contain part old, part new data) and validating all the data in the buffer.
Background
Main memory and register memory are used differently. Main memory is used for storing currently executing program logic whereas the register memory is used as a temporary memory by the currently executing logic.
Though register memory is a temporary one, since it is being used by the executing logic it is bound to contain some important variables that would affect the main logic.
Example
Examples for what could happen if this practice is not implemented:
(Reference: G. P. H. Sandaruwan, P. S. Ranaweera, Vladimir A. Oleshchuk, PLC Security and Critical Infrastructure Protection):
Siemens typically uses the scratchpad memory in the flag area from flag 200.0 to flag 255.7. If a bit is changed within this area there is a likelihood of a serious malfunction of the PLC based on the importance of that bit or byte.
Assume that an attacker can gain access to one of the machines in the PLC network and infect that machine with a worm which is capable of writing arbitrary values to the register memory. Since the register memory values changed arbitrarily, it can change the pressure value.
Executing logic will set a new value based on the change and that may cause the system to exceed its safety margins and possibly be driven to a failure.
Examples for implementing this practice:
In a scenario where there is a safety zone (but the DCS can read), the firewall can log any “write’ attempts with a rule that these registers are READ ONLY in the safety zone.
In another scenario, there could be some write-capable registers, and others are read-only, but having all the READ ONLY registers in a single array makes it easier to configure them in the controller (or a firewall).
Why?
| Beneficial for…? | Why? |
| Security | Makes it easier to protect the controller data by function (read/write/validate). Makes it easier for protocol-sensitive firewalls to do their job: The rules get simpler because it is very clear what register blocks are allowed for the HMI to access. Makes it easier to manage the (simpler) rules in the firewall. Making unauthorized changes to internal temporary memory is an easily exploitable vulnerability (By-pass Logic Attack). When inputs and outputs to PLC routines are properly validated, any changes (by a malicious actor or by mistake) can be caught easily instead of staying in the logic sequence for long and throwing errors / causing issues later in execution. |
| Reliability | Makes reads and writes go faster because the number of transactions is reduced. Even authorized changes and programming mistakes can cause a malfunction if temporary memory is not protected. Network and communications errors on long messages can result in unintended errors if the validity of the data is not checked prior to processing. |
| Maintenance | Programming mistakes causing writing to temporary memory can make it hard to find errors, so the problem can be avoided by assigning specific registers for writes. |
References
| Standard/framework | Mapping |
| MITRE ATT&CK for ICS | Tactic: TA009 – Inhibit Response Function, TA010 – Impair Process Control Technique: T0835 – Manipulate I/O image, T0836 – Modify Parameter |
| ISA 62443-3-3 | SR 3.4: Software and information integrity SR 3.5: Input Validation SR 3.6: Deterministic Output |
| ISA 62443-4-1 | SD-4: Secure design best practices SI-1: Security implementation review SI-2: Secure coding standards SVV-1: Security requirements testing |
| ISA 62443-4-2 | CR 3.4: Software and information integrity CR 3.5: Input Validation CR 3.6: Deterministic Output |
| MITRE CWE | CWE-787: Out-of-bounds Write CWE-653: Insufficient Compartmentalization |
Source: PLC Security