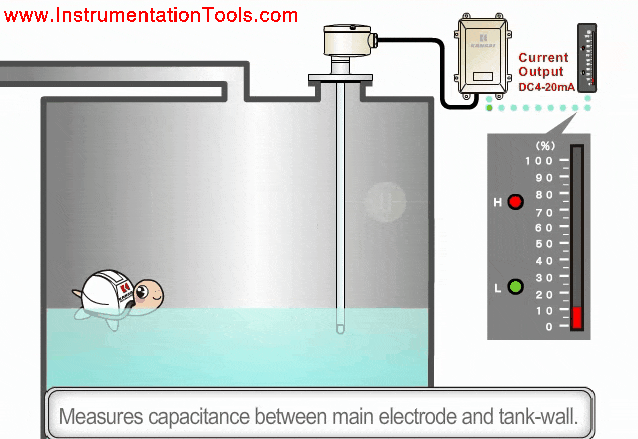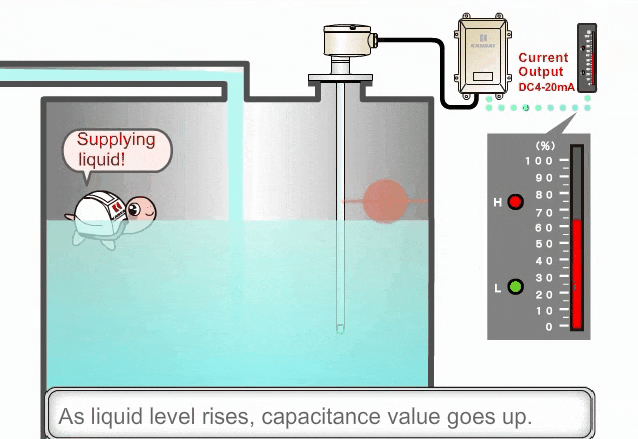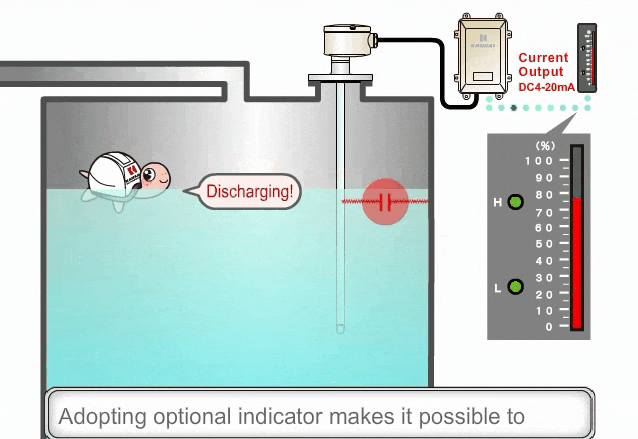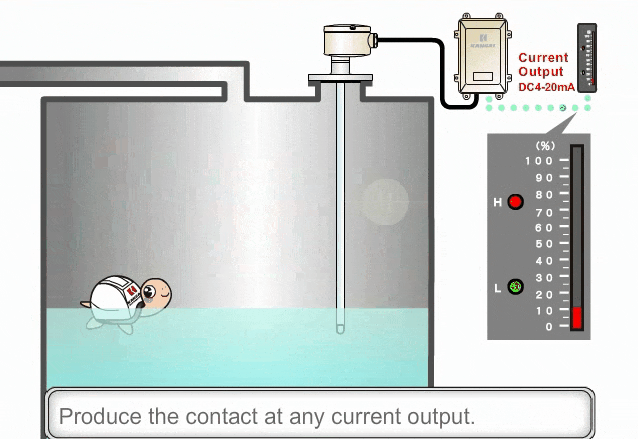
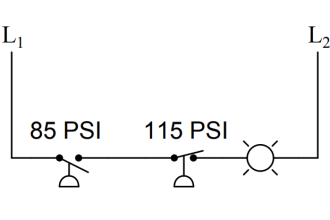
PLC controllers and network interface modules generally support multiple communication protocols that are enabled by default. Disable ports and protocols that are not required for the application.
| Security Objective | Target Group |
| Hardening | Integration / Maintenance Service Provider |
Disable Unused Communication Ports in PLC
Common protocols usually enabled by default are e.g., HTTP, HTTPS, SNMP, Telnet, FTP, MODBUS, PROFIBUS, EtherNet/IP, ICMP, etc.
The best practice is to develop a data flow diagram that depicts the required communications between the PLC and other components in the system.
The data flow diagram should show both the physical ports on the PLC as well as the logical networks they are connected to. For each physical port, a list of required network protocols should be identified and all others disabled.
Example
For example, many PLCs include an embedded web server for maintenance and troubleshooting. If this feature will not be used, if possible, it should be disabled as this could be an attack vector.
Why?
| Beneficial for…? | Why? |
| Security | Every enabled port and protocol adds to the PLC’s potential attack surface. The easiest way to make sure an attacker can’t use them for unauthorized communication is to disable them altogether. |
| Reliability | If a PLC cannot communicate via a certain port or protocol, this also reduces the potential amount of (malformed) traffic, be it malicious or not, which decreases the chances of the PLC crashing because of unintended/malformed communication packages. |
| Maintenance | Disabling unused ports and protocols also facilitate maintenance, because it reduces the PLC’s overall complexity. What’s not there does not need to be administrated or updated. |
References
| Standard/framework | Mapping |
| MITRE ATT&CK for ICS | Tactic: TA005 – Discovery Technique: T0808 – Control Device Identification, T0841 – Network Service Scanning, T0854 – Serial Connection Enumeration |
| ISA 62443-3-3 | SR 7.6: Network and security configuration settings SR 7.7: Least functionality |
| ISA 62443-4-2 | EDR 2.13: Use of physical diagnostic and test interfaces |
| ISA 62443-4-1 | SD-4: Secure design best practices SI-1: Security implementation review SVV-1: Security requirements testing |
Source: PLC Security