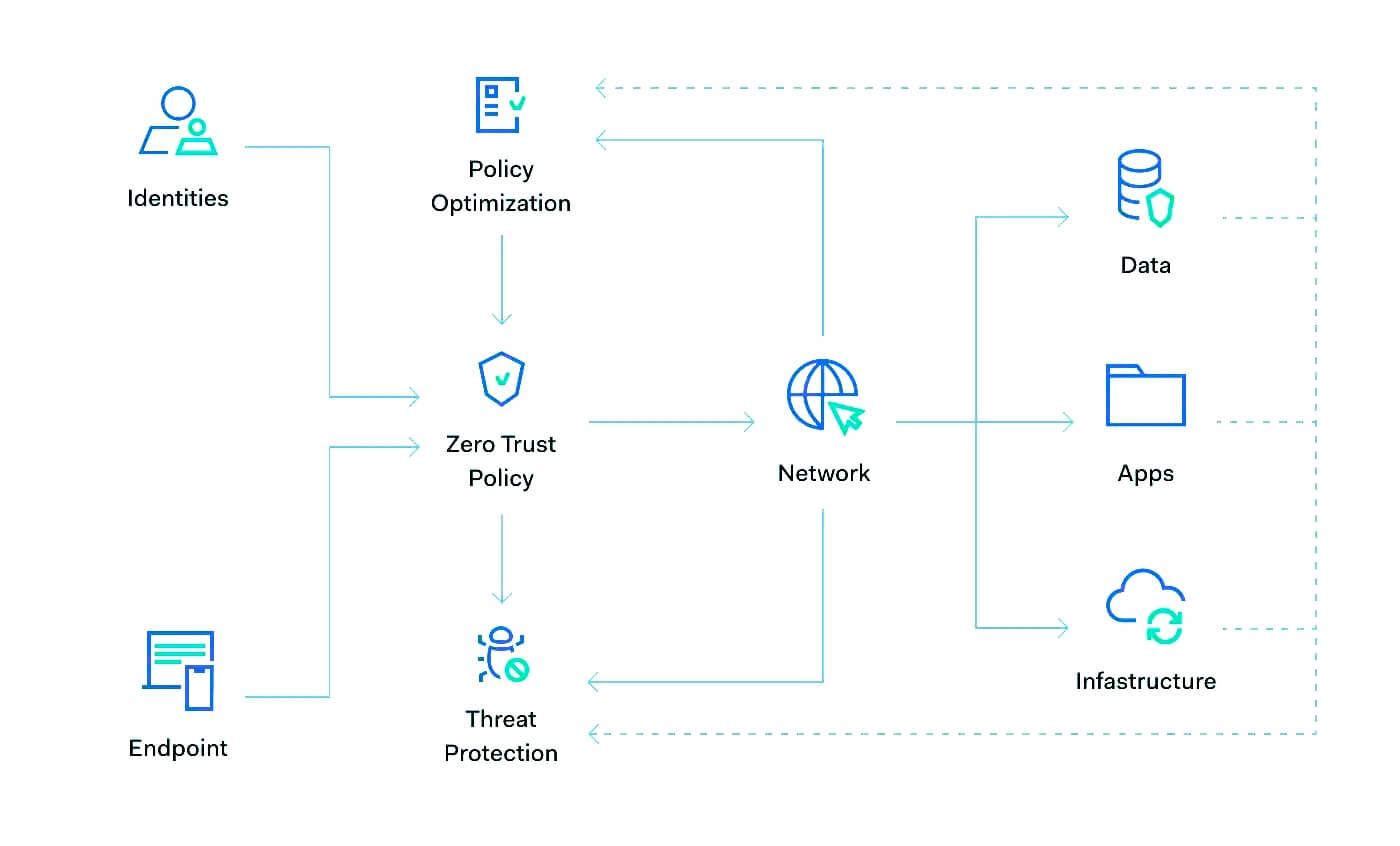
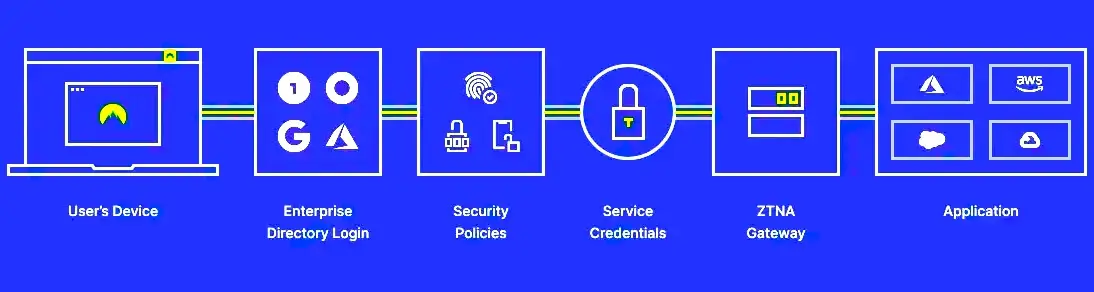
Zero Trust Network Access (ZTNA) uses Zero Trust security and serves as a cybersecurity technology. Although individuals do not need to use this kind of advanced technology for their daily activities, it is vital for companies to benefit from the latest protection technologies.
In this article, we will explain what is Zero Trust model and how the ZTNA solution can help organizations with their security issues.
What is Zero Trust Security?
Zero Trust technology reflects the idea of never trusting, always verifying. It is all about access permissions and regulations. Corporations can neglect access permissions and privileges at times.
This can cause them a disaster because each unauthorized access increases the risk of data leakage and cyber attack. With Zero Trust technology, all access authorizations can be regulated. Companies can decide on who can access which resources and can limit access permissions.
Giving a wide range of access permission to each employee accelerates security threats and makes your company network more vulnerable to attacks. For instance, when you give unnecessary access permission to your specific employees, they can make mistakes and put your resources in danger.
The best thing is to give adequate permissions to employees so they can only access the resources they need, not more. In this way, companies can narrow their attack surface and protect their vulnerable data from third parties or being stolen.
Zero Trust Network Access
Zero Trust security is not a single product that you can buy once and use. You should construct the available environment for Zero Trust implementations. Zero Trust technology requires regular audits, strict adherence to the rules, and employee education.
Companies that decided to implement Zero Trust technology and zero trust network access to their infrastructure should determine the necessities and weak points of their network first.
HR Role in ZTNA Management
Since cybersecurity methods have been developing, cyber threats and attack methods evolving simultaneously. This fact forces companies to take advanced security measures and use improved technologies. You have to take online security measures even if you are a small or medium-sized company. We live in a digital world that is full of cyber threats and reputation loss risks.
As a manager, you can determine access permissions and employee access requirements. Here, taking help from HR can be a good idea because HR is the most important part of employee and business relations. HR can give managers a broad overview of what employees need to access to maintain their work.
After classifying and matching resources and employees, you can restrict access permissions and take back unnecessary privileges. Then, focus more on your weak points. What are your most sensitive company assets? Do you use Cloud systems?
Why You Should Adopt ZTNA in Your Company?
Access Control & Risk Mitigation
We point out that access control is the most crucial part of any secure network. So ZTNA focuses on access control, permissions, and authentications to grant network security overall to the company.
Not only ZTNA protects networks but there are plenty of other solutions that companies can utilize. However, ZTNA shows up and demonstrates its power when it comes to large companies that are in trouble with access control.
Remote Work Security
Especially remote or hybrid work systems increase the importance of secure access solutions. There is no other way for the remote workforce to maintain their job but remote access to the company resources.
They require information, data, and other assets that are kept in HQ. When they can access all the resources even if they do need to, they increase the leakage risk and cause companies expensive consequences.
Network Monitoring
Thanks to ZTNA, company managers can choose authorizations and determine allowed users/ employees. They can put strict parameters and specify their criteria. It provides network visibility and great monitoring opportunity to the managers.
In addition to this, ZTNA enables managers to observe user activities. If they act suspiciously or have risk-increasing behaviors, managers can detect them and prevent risks before they happened. This is how ZTNA solution help companies overcome cybersecurity issues.
Identity Validation
Zero Trust Network Access gives importance to user validation to grant access security. Furthermore, it offers to separate applications from the network. It provides better risk prevention due to threat filtration.
When applications are considered apart from networks, cybercriminals can not reach the network easily. This feature adds another layer of protection to your security solution.
Data Protection
Data security is a prominent cybersecurity issue for many organizations. Companies have vulnerable, confidential, and vital personal data on their premises and cloud systems. This data should be protected from third parties or malicious attackers. If a company can not protect its data, it can lose its reputation and money.
Furthermore, business activities can be stopped due to the impossibility of running a business without the necessary data. We can say that data protection is vital for companies and they should take advanced security precautions and implement further protection solutions.
Zero Trust Network access facilitates remote workforce protection. Since remote employees pose a great risk to the company’s network security, companies need further solutions to protect their remote employees from any damage. ZTNA always asks for verification when a user attempts to access any company resources.
There is no difference between insiders and outsiders. ZTNA always controls access authentications and permissions. We know that most of the threats or risks are rooted in internal users so taking precautions only against third parties and outside users is not a good idea in terms of total security. Your workforce can also put your cybersecurity on the line.
This way, ZTNA lightens the burden of IT staff by facilitating remote access and employee access tendencies. It is more challenging for IT managers to control remote users when compared to on-premises employees. Here, ZTNA supports IT teams in their protection task.
Last Thoughts on ZTNA
ZTNA differs from other cybersecurity solutions due to its comprehensive protection opportunities. Organizations have more or less the same problems in terms of cybersecurity.
Although their requirements can be changed according to their size, budget, and the amount of vulnerable data; fundamentally they all need to protect their company resources from malicious attacks or any leakage.
Here, ZTNA offers advanced and effective cybersecurity solutions by using Zero Trust technology. Recognize the importance of access security and access control in your company then take the latest, effective, and proper precautions to avoid any damage.