As the need for additional process measurements increases, users seek a simple, reliable, secure and cost-effective method to deliver new measurement values to control systems without the need to run more wires. With process improvements, plant expansions, regulatory requirements and safety levels demands for additional measurements, users are looking to wireless technology for that solution.
With approximately 30 million HART devices installed and in service worldwide, HART technology is the most widely used field communication protocol for intelligent process instrumentation. With the additional capability of wireless communication, the legacy of benefits this powerful technology provides continues to deliver the operational insight users need to remain competitive.
Wireless HART
Backed by the Power of HART
- Built on proven industry standards
- Created by industry and technology experts
- Multi-vendor support and interoperable devices
- Uses existing devices, tools and knowledge
Flexible Applications
- Reduced installation costs – no wires!
- Process monitoring, control and asset management
- Health, safety and environmental compliance monitoring
Supports All Phases of the Plant Life Cycle
- Fast engineering, deployment and commissioning
- Cost-effective move from scheduled to predictive maintenance
- Easy diagnosing and troubleshooting
Simple. Reliable. Secure.
Even though millions of HART devices are installed worldwide, in most cases the valuable information they can provide is stranded in the devices. An estimated 85% of all installed HART devices are not being accessed to deliver device diagnostics information with only the Process Variable data communicated via the 4-20mA analog signal. This is often due to the cost and the difficulty of accessing the HART information.
WirelessHART technology allows users to access the vast amount of unused information stranded in these installed HART smart devices—85% of the installed HART devices. It also provides a simple, reliable and secure way to deploy new points of measurement and control without the wiring costs.
1. Simple
WirelessHART is a robust technology that is simple to implement. It enables users to quickly and easily gain the benefits of wireless technology while maintaining compatibility with existing HART devices, tools and systems.
Easy Installation and Commissioning
- Familiar tools, work flow and procedures
- Multiple power options
- Reduced installation and wiring costs
- Coexistence with other wireless networks
- Supports both star and mesh topologies
- Add devices one at a time
Automatic Network Features
- Self-organizing and self-healing
- Always-on security
- Adjusts as new instruments are added
- Adjusts to changes in plant infrastructure
2.Reliable
Industrial facilities with dense infrastructures, frequent movement of large equipment, changing conditions, or numerous sources of radio-frequency and electromagnetic interference may have communication challenges. WirelessHART includes several features to provide built-in 99.9% end-to-end reliability in all industrial environments.
Standard Radio with Channel Hopping
- Radios comply with IEEE 802.15.4-2006
- 2.4GHz license free frequency band
- “Hops” across channels to avoid interference
- Delivers high reliability in challenging radio environments
Coexistence with Other Wireless Networks
- Clear Channel Assessments tests for available channels
- Blacklisting avoids frequently used channels
- Optimizes bandwidth and radio time
- Time synchronization for on-time messaging
Self-Healing Network
- Adjusts communication paths for optimal performance
- Monitors paths for degradation and repairs itself
- Finds alternate paths around obstructions
- Mesh network and multiple access points
3.Secure
WirelessHART employs robust security measures to protect the network and secure the data at all times. These measures include the latest security techniques to provide the highest levels of protection available.
Protects Valuable Information
- Robust, multi-tiered, always-on security
- Industry standard 128-bit AES encryption
- Unique encryption key for each message
- Data integrity and device authentication
- Rotate encryption keys used to join the network
Protects Wireless Network
- Channel hopping
- Adjustable transmit power
- levels
- Multiple levels of security keys for access
- Indication of failed access attempts
- Reports message integrity failures
- Reports authentication failures
- Safe from Wi-Fi type Internet attacks
WirelessHART – How it works
WirelessHART is a wireless mesh network communications protocol for process automation applications. It adds wireless capabilities to the HART Protocol while maintaining compatibility with existing HART devices, commands, and tools.
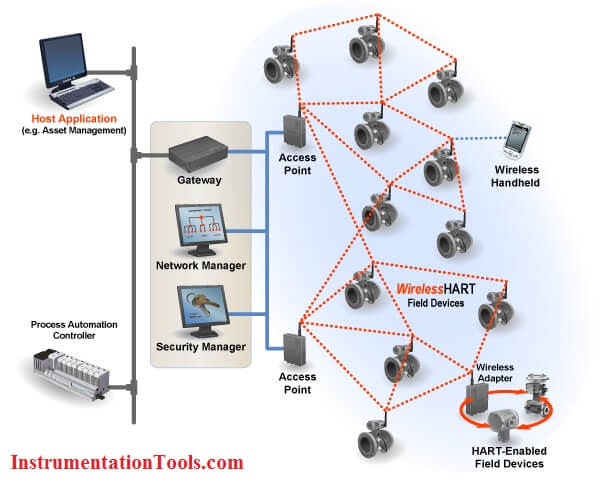
Each WirelessHART network includes three main elements:
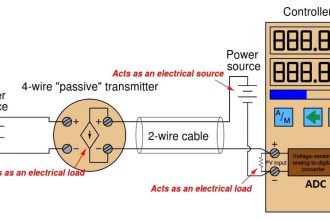
- Wireless field devices connected to process or plant equipment. This device could be a device with WirelessHART built in or an existing installed HART-enabled device with a WirelessHART adapter attached to it.
- Gateways enable communication between these devices and host applications connected to a high-speed backbone or other existing plant communications network.
- A Network Manager is responsible for configuring the network, scheduling communications between devices, managing message routes, and monitoring network health. The Network Manager can be integrated into the gateway, host application, or process automation controller.
The network uses IEEE 802.15.4 compatible radios operating in the 2.4GHz Industrial, Scientific, and Medical radio band. The radios employ direct-sequence spread spectrum technology and channel hopping for communication security and reliability, as well as TDMA synchronized, latency-controlled communications between devices on the network. This technology has been proven in field trials and real plant installations across a broad range of process control industries.
Each device in the mesh network can serve as a router for messages from other devices. In other words, a device doesn’t have to communicate directly to a gateway, but just forward its message to the next closest device. This extends the range of the network and provides redundant communication routes to increase reliability.
The Network Manager determines the redundant routes based on latency, efficiency and reliability. To ensure the redundant routes remain open and unobstructed, messages continuously alternate between the redundant paths. Consequently, like the Internet, if a message is unable to reach its destination by one path, it is automatically re-routed to follow a known-good, redundant path with no loss of data.
The mesh design also makes adding or moving devices easy. As long as a device is within range of others in the network, it can communicate.
For flexibility to meet different application requirements, the WirelessHART standard supports multiple messaging modes including one-way publishing of process and control values, spontaneous notification by exception, ad-hoc request/response, and auto-segmented block transfers of large data sets. These capabilities allow communications to be tailored to application requirements thereby reducing power usage and overhead.
Components of WirelessHART technology
A Gateway provides the connection to the host network. WirelessHART and then the main host interfaces such as Modbus – Profibus – Ethernet. The Gateway also provides the network manager and security manager (these functions can also exist at the host level – however initially they will be in the gateway)
The Network manager builds and maintains the MESH network. It identifies the best paths and manages distribution of slot time access (WirelessHART divides each second into 10msec slots) Slot access depends upon the required process value refresh rate and other access (alarm reporting – configuration changes) The Security manager manages and distributes security encryption keys. It also holds the list of authorized devices to join the network.
The Process includes measuring devices – the HART-enabled instrumentation.
A Repeater is a device which routes WirelessHART messages but may have no process connection of its own. Its main use would be to extend the range of aWirelessHART network or help “go around” an existing or new obstacle (New process vessel). All instruments in a WirelessHART network have routing capability which simplifies planning and implementation of a wireless network.
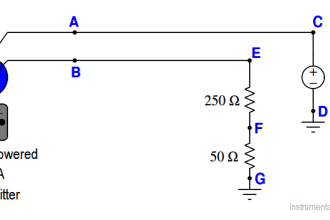
The Adapter is a device which plugs into an existing HART-enabled instrument to pass the instrument data through a WirelessHART network to the host. The adapter could be located anywhere along the instrument 4-20mA cable; it could be battery powered or obtain its power from the 4-20Ma cable. Some adapters will be battery powered and use the same battery to power the instrument as well – in this case there will be no 4-20mA signal to the host – all process data will be reported via WirelessHART
A Handheld Terminal may come in two versions. In the first case, the handheld will be a standard HART FSK configuration unit (just add new device DDs or DOF files), just like the one used for everyday tasks such as routine maintenance and calibration checks. In the case of wireless support, the handheld is used to join a new instrument to an existing WirelessHART network.
In the second case the handheld has a WirelessHART connection to the gateway and then down to an instrument and could be used for reading PV or diagnostics.
WirelessHART Security
WirelessHART employs robust Security measures to protect the network and secure the data at all times. These measures include the latest security techniques to provide the highest levels of protection available.
Protects Valuable Information – It’s Automatic
- Robust, multi-tiered, always-on security
- Industry standard 128-bit AES encryption
- Unique encryption key for each message
- Data integrity and device authentication
- Rotate encryption keys used to join the network – automatic or on-demand
Protects Wireless Network
- Channel hopping for security protection and co-existence
- Multiple levels of security keys for access
- Indication of failed access attempts – a rogue device
- Reports message integrity and authentication failures
- Safe from Wi-Fi type Internet attacks
WirelessHART technology was designed to enable secure industrial wireless sensor network communications while ensuring ease-of-use is not compromised.
Security is built in and cannot be disabled. Security is implemented with end-to-end sessions utilizing industry standard AES-128- bit encryption – approved by the National Security Agency (NSA) for top secret information. These sessions ensure that messages are enciphered such that only the final destination can decipher and utilize the payload created by a source device.
This means that no one can spy on your plant operations or inject “bad” or misleading process information.
Risk Assessment / Reduction To be a credible threat, an attacker must possess access, knowledge, and motivation. The WirelessHART technology Security architecture helps users address all three of these areas:
• Minimize, control, and audit access • Require high levels of technical expertise to subverted • Reduce the consequences (span and duration) of any individual security breach
Wireless Sensor Network Security can be broken down into two main categories:
- Data Security or Confidentiality deals with maintaining the Privacy and Integrity of the information being passed over the network.
- Network Security or Availability deals with maintaining the functionality of the network in the face of internal and/or external attacks (intentional or unintentional).
Data Security

Security features associated with privacy aim to prevent eavesdropping by unauthorized devices inside or outside the network. AWirelessHART sensor network provides end-to-end CCM mode 128-bit AES encryption at the network/transport layer from the data source to the data consumer – the Gateway.
In addition to individual session keys, a common network encryption key is shared among all devices on a network to facilitate broadcast activity as needed. Encryption keys can be rotated as dictated by plant security policy to provide an even higher level of protection.
A separate 128-bit join encryption key is used to keep data private that is sent and received during the joining process.
- The join key serves as authentication to the Security Manager that the device belongs to this network.
- The join key is treated separately from the other keys to enhance Security.
- Join keys can either be unique to each device, or be common to a given WirelessHART network based on the user security policies.
- Join keys can be changed after the device joins the network to further increase security.

Data Security features associated with Integrity ensures that data sent over the wireless sensor network has not been tampered with or falsified.
- WirelessHART uses a Message Integrity Check Field that is added to each packet.
- The receiving device uses this Field along with the protected data to confirm that the contents of the packet have not been altered.
- This Field protects the network routing information preventing attacks that attempt to change the packet’s network/transport layer information.
Data Integrity also involves verifying that the packet has come from the correct source. The network/transport layer message integrity check field, the information used to generate the check field, and the sender/receiver unique session key that codes and decodes the data are tools that can be used to verify the source.
Network Security
A wireless sensor network also needs tools to protect it against attacks. These attacks can attempt to compromise the network by inserting Trojan horse devices, impersonating networks to get sensitive data from legitimate devices, and disrupting the network to deny service. Attacks can be launched from outside or inside the company by external people or employees.
Network Security depends upon techniques to support Authentication, Authorization and Attack Detection.

A WirelessHART Gateway and the wireless sensors joining the network must be configured to control which devices are allowed to access the network. The network will only be secure if all the devices in the wireless network maintain security.
- A WirelessHART Gateway has a secure authentication process which it uses to negotiate with all joining devices to ensure they are legitimate.
- As with all other network communications, all join negotiation traffic is encrypted end-to-end.
Denial of service attacks are aimed at impairing the proper operation of the system by interfering with communications within the wireless sensor network. These attacks may try to jam the radio or they may try to overload a process like packet acknowledgments.
- WirelessHART devices can report anomalous conditions that might signal a denial of service attack, such as traffic counters, retransmissions, etc.
- WirelessHART devices can be network routers or just data sources – user configurable – but only messages that authenticate are routed onward and discarded if it fails the security checks.
- WirelessHART devices are not authorized to be network key servers or wireless network managers.
An important point to know is that a WirelessHART sensor network does NOT implement the TCP/IP (Internet) communications stack, and thus is explicitly safe from many typical hacker attacks.
Join, network and session keys must be provided to the WirelessHART Network Manager…and join keys must be provided to Network Devices. These keys are used for device authentication and encryption of data in the network.
The WirelessHART Security Manager is responsible for the generation, storage, and management of these keys.
There is one Security Manager associated with each WirelessHART Network. The Security Manager may be a centralized function in some plant automation networks, servicing more than just one WirelessHART Network and in some cases other networks and applications.
Source – Fieldcommgroup