Data transmitted and received through the internet requires security from hackers. It cannot be transmitted as it is in the raw form, otherwise there are high chances of data getting corrupted. So, a set of protocols and rules are required to protect the internet data. Be it WiFi or Ethernet, IP addresses used in the devices are responsible for identifying each device and communicating data. The protocol used for protecting data over the Internet is called IPSec. In this post, we will see the concept of IPSec.
Why is IPSec important?
IPSec stands for Internet Protocol security. As the name implies, it is used to define a set of rules and protocols for protecting data communicated over an internet network. If the data being sent is critical and without any protection, then anyone on the internet could access and steal the data. For this purpose, IPSec is used to secure the data by enclosing them in various keys and encryption methods. Due to this, it becomes difficult for hackers to hack the data communicated over the internet. All the received data packets are authorized and it is ensured that it is not being received from unknown sources.
How does IPSec work?
IPSec works in two phases using internet key exchange or IKE. As discussed before, keys play an important role in encrypting data, and no one can easily unlock it. It is virtually impossible. So, the data in IPSec is authenticated and encrypted using keys, and it does this through a tunneling method. Tunneling method means creating tunnels inside the network, so that the data does not remain open.
There are two tunnels created; the outer tunnel will encrypt data for auto-negotiation or identification of two devices, and the inner tunnel will encrypt the actual data to be communicated. Tunneling is a concept; practically, it works by insertion of keys. Keys are a string of random characters that are generated by the network and both the devices should know them, so that the sender can encrypt data properly and the receiver can decrypt data properly.
The most used protocol in IPSec is ESP or encapsulating security payload. This protocol is widely used because it serves all the purposes of authentication, data integrity and security encryption. Due to this, both the sender and receiver parties are assured of correct data and it is not being lost in between. The other less used protocols are authentication header (AH) and security association (SA). Remember that IPSec works directly on the network layer of the OSI model.
IPSec connection establishment process
The connection mode in IPSec is pretty much simple. As discussed earlier, they first need to identify themselves on the network and decide how the data is going to be protected, by creating key sets for the outer tunnel. Without identification, it is obvious that they cannot communicate packets between correct addresses (Note that data is communicated in packets or small chunks, and not one whole data format). This is the first step in creating an outer tunnel as discussed before.
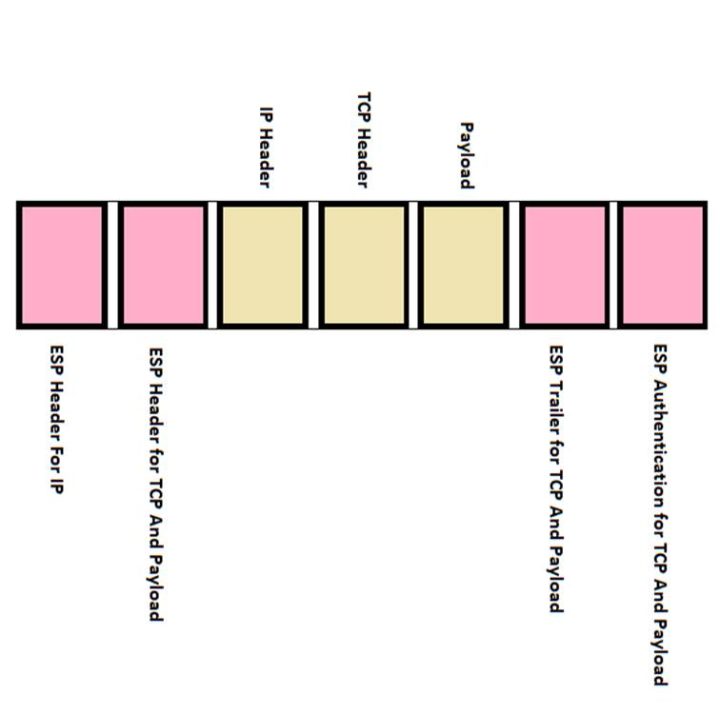
Now, the next task comes to encrypt actual data, which is in the form of three parts – IP header (containing IP addresses of both the devices), TCP header ( containing port numbers and sequence numbers of both the devices) and the payload (actual data).
As you can see in the below image, these three parts are covered before and after with various keys or ESP protocol data. The left hand ones are headers and right hand ones are trailers. Once both the tunnels have been created, data communication starts with proper authentication, encryption, decryption and integrity. This tunneling method is the most used one in IPSec for efficient communication.
In this way, we saw the concept of IPSec.
Read Next:
- Factors to Calculate Network Speed
- What is Auto-negotiation in Network?
- Timeout in Communication Protocols
- Difference Between Subnet and VLAN
- What is a Patch Panel? Types and Uses